
When faced with increasingly pervasive and direct surveillance, how can peaceful individuals turn the tables on predatory practices to safeguard their privacy in an interconnected society?
This essay is the practical sequel to the theory implied in “Four Wolves and a Rabbit”. As stated there, although it can be played on a checker board, it has direct application in the real world. That brief exploration of game theory was an introduction to professional surveillance methods and, more importantly, how to mitigate or evade them. What follows here is an example, drawn from my lived experience.
In an era of increasing technological sophistication, the intersection of privacy rights and surveillance is a touchstone for societal and legal discourse. Although I am a hunter and gatherer of intelligence, my motivation to acquire the skillset was not merely commercial, as it might have been for — shall we say? — a locksmith. Actually, depending on location, business model and client base, most people can make a more comfortable living by installing or defeating physical locks than they can by discovering what is lost and/or hidden by human hearts and minds.
A PREDICAMENT
My interest in the OSINT trade was initially inspired by an affirmative defense of eroding civil liberties but, on account of other skills I’d already acquired over the years, it branched out first toward IoT (internet-of-things) and then to Fintech in its search of commercial application. However, when I noticed a suspicious driver conspicuously following my left flank recently, neither circuit boards nor financial fraud were the first thing to cross my mind.
Indeed, although I was not surprised or scared to be tailed by a fellow Private Investigator (PI, a recurring acronym in this narrative), I was rightfully angry since I was driving my wife’s car … she was the prey!
Naturally, I confirmed the tail before hopping to conclusions. I would not have seen it if I had been the passenger, of course, nor would my wife have recognized the signs if she had been the driver. Yet experience shows that the most interesting things happen precisely where luck collides with preparation.

By degrees, this essay aims to introduce the lay-person to retail counter-surveillance, albeit indirectly, leaving room to run. First, however, unless you or yours have been stalked before, there is a case to be made for enhanced situational awareness in mundane urban environments, which I regret because it’s a case that should make itself. Eventually it will, when its sorry lack claims enough victims.
Let that land …
No matter how urgently one advocates for awareness, though, without help and constant coaxing, average people tend to learn the hard way, and subaverage people make it even harder still. On a more recent occasion, a related circumstance forced us to dip into our Private Insurance (PI) and sell some Krugerrands to pay for emergency Professional Insight (PI), which is never inexpensive. There, too, in the parking lot of the local coin shop, she saw no reason to treat the errand any differently than a trip to Starbucks or Chipotle Grill.
She’s learning, and you can, too.
THE PEN
Although the legal landscape governing surveillance by PIs is complex, and varies by jurisdiction, laws everywhere (in the Western world) generally agree that it must be conducted fairly, transparently and with the subject’s rights firmly protected. Trespassing, harassment, or unauthorized data collection are expressly illegal, and can lead to a range of consequences from civil liability for invasion of privacy to stickier criminal charges.
To adhere to legal boundaries concerning physical surveillance, PIs must first ensure that they have legitimate grounds, and are often required to obtain necessary permissions, especially when monitoring individuals in private spaces or sensitive situations. Trespassing on private property, installing cameras or listening devices without consent, and following individuals too closely can cross into illegal territory, leading to charges of harassment or stalking.
Such tactics can and should result in criminal charges, civil lawsuits for invasion of privacy, and potential professional consequences such as the revocation of a PI’s license. The not-so obvious reason is that, unbeknownst to the public at large, law enforcement personnel are held to the same standard, although their far-too frequent crimes are much more difficult to prove in practice.
Clients who hire PIs also bear responsibility for their ethics and intentions, and are ill-advised to outsource any potential bad deeds of their own, even to the willing. Any negligence (or nepotism) of theirs can compromise the legal standing of private surveillance, and reflect ethically and legally back upon them. As the motive behind the means, they must hire operators who respect both the letter and the spirit of the law.
Fortunately, a higher percentage of PIs respect legal limits than do their counterparts in law enforcement itself, who privately use qualified immunity the way surgeons use disposable gloves.
These are the murky waters of physical surveillance, and PIs lurk online, too. Therefore, arming yourself with the legal tools and technical tactics to dodge their prying gaze means, first, even before understanding your adversary, surveying the battleground itself. In the real world, the advantage goes to whomever uses the terrain best, and the contest is always fluid.
As tempting as it might be to think of this as a game of cat-and-mouse, regular readers of my work already know why I refer to the physical action space of surveillance as The Pen. If your senses leave you feeling cornered, then the feline analogy is a luxury that you cannot afford, since cats don’t hunt in packs.
THE WOLVES
Can you imagine the fabric of your life, your basic everyday hustle and bustle as a vast, sunlit field? If so, then you might be on the menu, for what now appears as a field is, in fact, a Pen. That is how hunters, human or otherwise, see the field, after all, which is to say that victimhood is a voluntary state of mind, regardless of victory or defeat.
How YOU see it is a matter of choice, of course, yet once you verify that you are a target, ignoring the scrutiny upon you can be dangerous since it belies intent, whether or not you know whose.
In effect, PIs are a pack of keen-eyed Wolves that blends seamlessly into the tall grass, foot soldiers in a landscape of surveillance capitalism, each employing their own subtle tactics to track and understand the Rabbit (you, or another) without disturbing the peace in the Pen.
The Wolves are stealthy, though, and don’t just watch, They move, on multiple fronts, quietly and with purpose. These are not isolated incidents but a coordinated pack effort, painting a picture of your habits and secrets.
Telephonic surveillance is not out of the question, of course, and not just during calls. That digital appendage of yours can betray you with each benign buzz and every creepy click, or with those randomly untimely battery drains. Glitches are the whispers hinting that you might have company.
Do not be surprised to find Wolves conducting banter-based surveillance, either — idle strangers with an unhealthy interest in your unremarkable life, casually fishing for tidbits like a well-meaning but senile old aunt at a family reunion. As they purposefully weave through your day, seemingly disguising disinterest, they are “data mining” for flecks of golden dust in your leaden responses … or others’.
And what long noses those Wolves have, too; all the better to sniff around your waste bin.
If documents about yourself that not even your intimates are aware of should return suddenly to haunt you like the Ghost of Christmas Past, then cue the dramatic music and get ready for fight or flight. Those aren’t just any old papers, after all, but the breadcrumbs left by someone piecing together the puzzle of your life, perhaps overstepping those blurry lines of legalese.
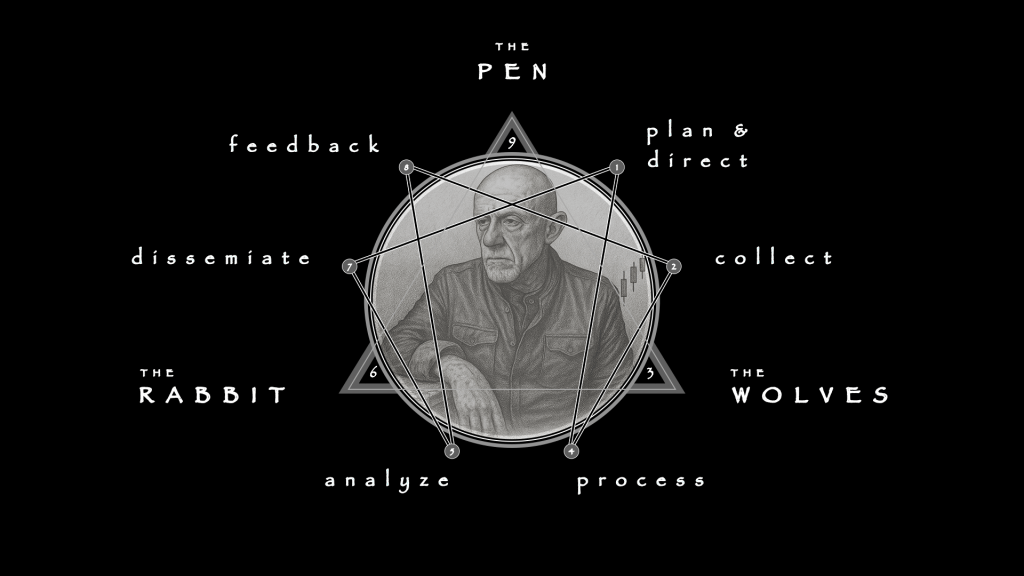
1. PLAN & DIRECT
The first step is to see the Pen for what it is, unapologetically and in its entirety. Understanding every corner where a Wolf might hide. Learn the tools of the trade — the techniques and technologies that they all use to stay upwind from a Rabbit. Don’t worry about evasion or other countermeasures, not yet. Just map the terrain, from the physical to the digital … to the emotional.
2. COLLECT
Next, gather specific environmental cues, i.e. how the local Wolves mark their territory, depending on their specializations. Like you, they leave signs of their presence, and of their passing — droppings, to press the analogy. Oddly situated vehicles are an obvious example. Strangers with an unusually good memory for details may be less obvious, especially if you tend to be agreeable and/or speak too freely. Note every rustle in the grass, every odd reflection of light during the collection phase; no detail is unimportant. Identify the white spaces around you, for they may prove to be the most pivotal of places later.
4. PROCESS
Now, categorize those whispers among the grass, each shadow in the trees. Select and arrange your findings into a coherent guide to the Wolves’ behavior, a Field Manual, if you will. This step involves crafting a clear, accessible depiction of the surveillance ecosystem, from the blunt snout of a camera lens or the pointed tips of a covert microphone to the schedules of your mail delivery, your trash pick up … or that friendly milkman.
5. ANALYZE
Here, the effectiveness of each Wolf, and each method, is evaluated, not just how they hunt, but where … urban jungles, rural expanses, online? What strategies do the Wolves use in their preferred terrain, and how might they react if flushed out? This is where patterns emerge, and the behavior of the pack becomes predictable. Remember those white spaces? Those transitional zones are where evasions are most effective, and where traps are most effectively set.
7. DISSEMINATE
Share your knowledge of lupine lore and of the Pen — pay it forward far and wide. It could be a series of detailed videos or articles, such as this, or a comprehensive guide, depending on how the Rabbits in your network prefer to consume their content-carrots. Not only will you be helping others in need; your own claws will grow to make a better digger of you, and those fabled little Rabbit fangs of yours might sprout, too.
8. FEEDBACK
Finally, figure out if your evaluation of the Pen resonates with other possibly bewildered Rabbits in your network — and even with some of the Wolves. Yes, you read that right. Interviewing a few and, in some cases, possibly even hiring one can only make you a more informed individual. Also, integrating the opinions of legal eagles and the actionable insights from the more seasoned hares can refine and perfect your perspective of the Pen.
THE RABBIT
When you feel the hairs on the back of your neck stand up from the prick of unseen eyes on your skin, you might be the star of your very own spy flick. If so, the stakes are real, and the audience is unfriendly. Congratulations on opening your eyes.
Now what?
First, breathe. Panic is the cologne of the hunted; it smells like shit and it gives you away. Stay cool, stay sharp. From now on, unless and until you are certain that the threat is no more, every move you make must be calculated.
THEY ARE NOT REAL WOLVES — THEY WILL NOT EAT YOU.
Their primary goal is to acquire information, which they cannot do if they are detected. That is their weakness, and your advantage. They, too, are hiding, after all, with both their reputation and their livelihood on the line.
So, document every brush with the bizarre. The unfamiliar SUV that’s a little too fond of your street, or a phone that might listen more than it speaks, these notes are your first line of defense, the rough sketches of your map of the Pen. Gobble up those details and finish that Rabbit’s crash-course Field Manual to dodging (and eventually hunting) Wolves in the wilds of the postmodern surveillance savannah.
Change it up, too, be unpredictable. If you normally grab coffee at 8 AM, throw a curveball — maybe one at noon instead, or a slow breakfast at a cafe you don’t like. Your surveillance detail will sidle up alongside of you, adjusting to your new rhythms. This dance is your chance to flush the Wolves out so, instead of fleeing; zig where you normally zag, and ID your targets.
Electronic eyes and ears might be harder to spot, but they do leave traces. Unusual data spikes are a clue, or rapidly draining batteries. Encryption is your best friend here, your cloak to their dagger. Also, if you haven’t begun already, assume that your devices are listening to you, and be selective (and even dynamically misleading) in your speech.
Reportage is key.
Let the cops know of your unwanted fans. Police can shine the spotlight onto those who shadow you. If a PI turns your hum-drum daytime drama into an episode of a bad detective series, your lawyer might just write them off the show. Nothing scares a Wolf like a sharp subpoena.
Finally, team up (more on that below). There’s safety in numbers, obviously, but greater insight, too. Four eyes can see more than two, and six see even more than four. A wingman or two can dissuade the more opportunistic tails out there and/or give you a perspective on your paranoia, to discern if you’re really a person-of-interest or just over-caffeinated.
No matter what, though, do not ignore your instincts, which you have for a reason — if you feel uneasy, trust yourself that something might be wrong, and act accordingly.
Never forget that the way of Personal Incentive (PI) is as universal as it is unreliable. The superior Way of the Rabbit is run by virtue of Preemptive Initiative (PI). With that as your dagger to their cloak, maybe, just maybe, the Wolves will have bitten off more than they can chew.
COUNTERMEASURES
I discuss the surveillance predicament in terms of the Pen, the Wolves and the Rabbit because it grounds the subject (potentially you) thematically in a contest decided not by strength but by information. The description is static, though, whereas the reality is fluid, ergo some indication of concrete practical steps is needed.
As a flowchart, the enneagram synthesizes dynamism and coalescence, making it useful in this case, too. It unites the disparate elements of a process into a system of three sources — the Logos — and six steps, which I will briefly enumerate.

Again, my purpose here is to instruct Rabbits to counter a certain class of Wolf pack tactics. If instead — let us say — it were to train novice PIs to work together to avoid detection, the six steps would be entirely different, even with a similar Logos.
Furthermore, each particular step is described in broad terms. The treatment is not exhaustive, but suggestive.
The point, as I alluded above, is that each of these is worthy of longer form content, be it a separate post (blog or video), for example, or a chapter of a book. Of course I hope to fill in some of those blanks myself, however the field is a Pandora’s Box. Once opened, your best bet is to go where your curiosity takes you, and not to seek a prescribed path.
My own subjective areas of interest (above) lie more in points 1, 5 and 7, however your own situation may leave you with a different focus or set of needs.
1. SURVEILLANCE DETECTION ROUTES (SDRs)
Vary your schedule as much as possible and avoid convenient navigation; take the long way. Surveillance teams may set up shop along a route that you frequent. By casually altering your habits, your movements become less predictable. I keep mentioning those white spaces for a reason and, depending on your routines, red spaces may also be available to you, filters and bottlenecks that limit your tail’s passage.
One idea is to visit a mundane well-lit, high-visibility location for 10-15 minutes, like a donut shop, then drive in a small circle back to the same place and stay awhile longer. A second idea is to randomly exit and reenter the same freeway … more than once. Yet a third idea is to throw out your trash, especially your paper recycling (pre-shredded, of course) on the morning of collection, not before.
Game it out, and have some fun.
2. DISGUISE & DECEPTION
Conduct a wardrobe change in a secluded place. This could be as simple as ditching a coat, donning on a hat, or changing your shoes … or not. A good surveillance team will note your footwear; now you know. If you think you may need to run, consider wearing sandals to begin and changing into shoes before the chase. Reversible coats are ideal, and wearing removable layers is a fine substitute in many situations.
The challenges of video surveillance are greater and more subtle, especially if you factor in CCTV feeds and sophisticated software. Operators can scroll between locations, or forward and backward in time, and even learn to recognize your stride. Your options will depend on who is watching you. Circumstantial make-up or prosthetics are ill-advised, especially if your tail is official, and only a matter of last resort.
If you have nothing to hide, then standing in plain sight may be your safest choice.
4. ELECTRONIC / DIGITAL FOOTPRINT
“Bugs” emit electromagnetic radiation, usually radio waves. TSCMs (Technical Surveillance Countermeasures) sweep for them with an appropriate detector, a device that measures the strength and direction of their RF signals. If you are a standing target, though, maybe managing a business or other sensitive operation, then SDSs (Surveillance Detection Systems) are your analog to SDRs, digital watchdogs built to warn of potential intrusions by sensing unusual behavior.
Similarly, WIDS (Wireless Intrusion Detection Systems) safeguard wireless networks by identifying unauthorized devices attempting to breach your digital perimeter. Your data is your digital DNA — unique, private, and valuable. Strong passwords, encryption, and secure networks are your digital deadbolts. If needed, signal jammers and lens detectors can further help you to maintain your privacy.
In the digital age, paranoia is the new pragmatism; the less you leave behind, the less there is to find.
5. EVASION
Avoid risky locations, of course, and be more discreet and circumspect than those around you. Common sense will not be enough, though, in the moment of evasion, which is why you made such tasty Wolf jerky from all that raw data. And it is merely a moment that you will have, so plan ahead. Assuming that your tail is working as a team, you will be easily reacquired if you choose your time and place at random … so don’t.
Challenges vary if you are on foot or if you are driving. (Even worse would be if you are a passenger, but that’s a highly specialized problem of its own.) In either case, keep your cards close to your chest, and don’t tell on yourself before you make your move. Meanwhile, use that vast, sunlit field of your basic everyday hustle and bustle as background noise to keep prying eyes and ears at bay.
Even more than risky locations, avoiding risky (i.e. unpracticed) moves is a tactic that should need no explanation.
7. COUNTERSURVEILLANCE
In this game of hide and seek, where your privacy is the prize, winning means ensuring that your private life remains just that—private. Although there are, of course, apps and devices to detect bugs, GPS trackers, or hidden cameras, reliable countersurveillance requires a complete lifestyle adjustment based on situational awareness, and up-to-date knowledge of professional practices. At a minimum, start browsing websites that market such products (but resist the temptation to buy toys that you don’t need), to understand your adversary.
Online forums, privacy advocates and specialized newsfeeds can provide valuable insights and updates on the latest in privacy technology and surveillance tactics. Keeping an open mind will be difficult, but vital; again, map your threat-vectors, especially the emotional. Worse, there is no substitute for initiative here, and laziness is the enemy. Teamwork mitigates the workload, if you are blessed with motivated people in your midst — training your family to care can be a blessing or a curse, depending on how you present it to them. It’s such an unpredictable journey, so full of discoveries (many of them unpleasant), that generalities are the extent of the present survey.
Most importantly, though, remember that the pinnacle of countersurveillance is not mere evasion, but the gathering of intelligence of your own.
8. PROFESSIONAL INSIGHT
If you suspect that more sophisticated surveillance methods are at work against you, then consider fighting fire with a ton of bricks. Hiring a counter-surveillance expert is the unbeatable move, but just as with disguise or evasion, extremes should be avoided. They can equip and train you to detect electronic surveillance devices, and even provide more advanced counter-surveillance services if needed.
Although vetting is a separate subject unto itself, first be prepared for a battery of of tough questions. If you have been filtering your problem through the Intelligence Cycle (have you tested my free Custom AI Tool?), then you should already know a lot about who is watching you, as well as how (as in where and when), and why (what is their definition of success?). The specific Logos will dictate what kind of professional you should seek, and exactly what questions you should be asking each other.
It’s all-too easy here to say “choose wisely”, which is always difficult for lay-persons to do when hiring specialists — of any kind, including plumbers — therefore my advice instead is to figure out your limits in advance to avoid surprises.

Countersurveillance measures are those taken to prevent, detect, and mitigate unwanted surveillance activities. Remember, though, that while these can help you to proactively manage the irritant, you must act within the law and especially avoid causing harm to others.
Once you cross that Rubicon, among other disavowed hazards, then you are no longer practicing countersurveillance, and risk drawing attention to yourself in the process of whatever you’re doing instead.
The one and only aim is to inform yourself, not to remove adversaries. Strictly speaking, the Wolves are not your true opponent; they’re just doing a job. Like plumbers, ironically, they are worthy of every professional courtesy, even if you compete against them. It is their client, after all, who matters.
Most importantly, though, making enemies gives you no new information.
Leave a comment