Every stable system—whether a courtroom, a poker table, or even a playground—rests on a few non-negotiable rules. Break them, and the scene collapses into force (+), theft (-), or deception (0). The Law of Three gives us the geometry to see these rules not as moral slogans but as structural positions in a working process.
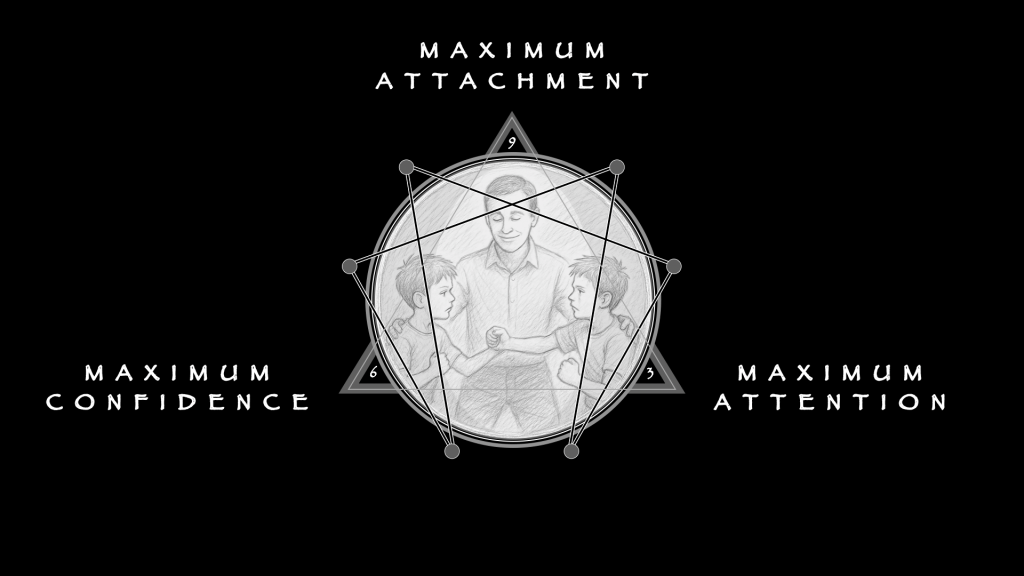
The process described here is a 132 triad, or Concentration.
The order of operation of the forces is affirming (+) first, then reconciling (0), then denying (-). This is the holding pattern that contains energy long enough to enable cooperation under pressure. Once you see how the rules sit in this frame, you will begin to be able to see them anywhere and everywhere, from sandbox disputes to street fights … to free advice on a train bound for nowhere, bestowed on a debutant by an aging gambler.
Three Universal Rules
The following are timeless and universal, and yet nobody can seem to name them. When you announce (i.e. remind them of) these cardinal points, they always claim to remember with an “Oh yeah,” as if it were obvious. Ironically, it is obvious because some version of these rules is written on every kindergarten wall, which are older than language itself.
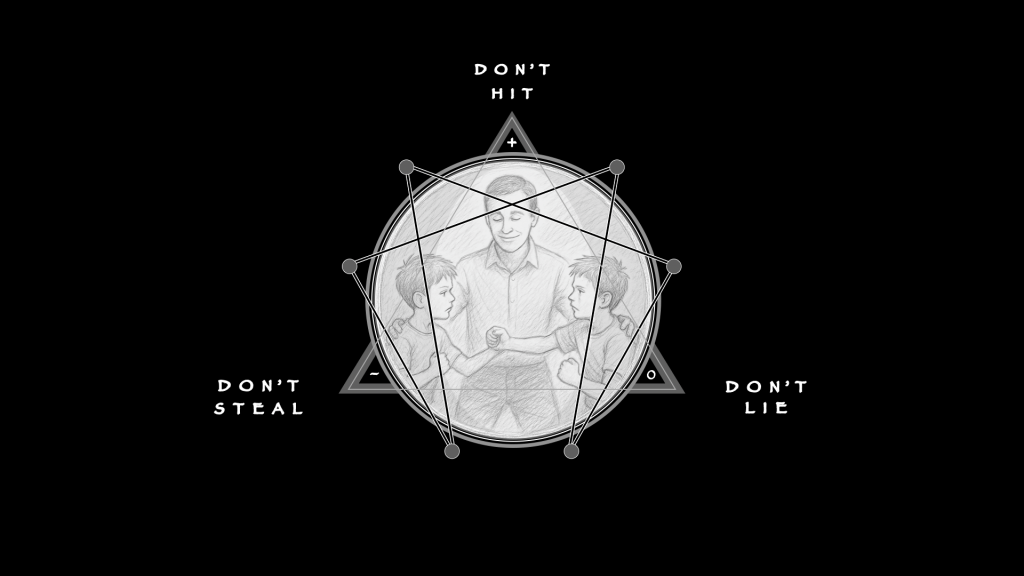
On the enneagram of Child’s Play, “Don’t Hit” belongs at the zenith, the point of maximum attachment, the stone that caps escalation so that the rest of the field can hold. “Don’t Lie” belongs at 3, the point of maximum attention, where the truth channel either stabilizes the whole or poisons it instantly. “Don’t Steal” belongs at 6, the point of maximum confidence, where investment occurs only if property and effort remain secure.
This is not sentiment; it is field geometry. Each position contains a force. Each rule is the fitted instrument to make that force work in the real world.
“Don’t Hit” … The Hard Stop on Kinetic Force
This first and most important rule prevents an argument from becoming a war. To cross it triggers an escalation that neither party can fully control—return blows (+), third-party intervention (0), and a frame change that forgets (-) the original grievance.
For girls, physical contact is fairly rare, escalation paths tend to be relational, and separation by an authority figure—male or female—usually resets the board. The rule always applies, of course, but the enforcement (+) channel can become reputational (0) because the physical risk (-) is lower.
For boys, the significance is deeper: their disputes sit closer to the ancient male role of hunting, defense, and the credible threat of violence. Physical escalation can pass the injury threshold in seconds. Male enforcement (+) is absolutely essential here because it carries the same evolutionary currency of credible force; boys recognize boundaries (0) set by someone who could, if pressed (-), operate (+) in the same medium.
“Don’t Lie” … The Reconciliation Bridge
At the position of maximum attention, your account, your word (0), either lets force (+) and resistance (-) meet without collapse or else it rots the bridge.
For girls, lies may target alliances and reputations (“She said you’re not invited”), eroding trust more slowly but still undermining the truth channel (0). Enforcement (+) in such cases is about restoring cohesion (0) over time, not managing imminent bodily risk (-). In both contexts, this rule exists to keep communication (0) clean enough that the other two rules can function.
For boys, a false claim in the heat of a dispute (0) (“He hit me first”) can immediately change who is justified in using force (+), or recruit allies under false pretenses (-). The result can be instant escalation. Male guidance matters here because it understands the combat-prep implications: misinformation (-) is not a harmless trick (“Just playing”)—it is a live action (+) that can provoke or justify physical retaliation.
“Don’t Steal” … The Property Lock
If your work (+) can be taken without (-) your consent (0), your time horizon collapses.
For girls, theft (-) is often symbolic—borrowing clothes, taking personal items—and the harm plays out socially rather than physically. Restitution and mediated agreement (0) are usually enough to restore confidence (-). For either gender, the damage is the same: if property rights are not defended, planning shrinks, quality drops (-), and the willingness (+) to bring good resources to the table (0) dies.
For boys, theft (-) can provoke immediate recovery attempts—chasing, tackling, grabbing—that risk re-entering the domain of force (+). The confidence field breaks quickly, and without credible enforcement it rarely comes back. Here again, male authority often has an advantage in reading whether recovery (-) force (+) is imminent and in commanding the respect (0) needed to stop it.
A Concrete Scene Shows the Map in Motion.
Two boys are building a fort. A prized cushion is grabbed. Without a modeled channel for assertion, the urge is to throw hands. If that happens, the field is gone. The hit invites a hit back. Adults arbitrate harm instead of property. The fort collapses into noise. To apply the affirming force (+) here is the better move: state the claim, offer a trade, appeal to the referee if needed. If the other child lies—“He gave it to me”—the scene moves to 3. The referee’s job is to protect the truth channel (0), not to moralize. A small, immediate cost for a false report keeps the bridge intact. If theft stands in the name of “sharing,” 6 collapses quietly; no one brings good materials next time, and the game contracts into junk pieces.
Property rights at 6 matter because they lengthen time. In this geometry, “Don’t Steal” is not an ideological plank—it is the only way to preserve a planning horizon. Forced sharing and predation are functionally identical to the person losing the asset. Both destroy confidence. Both teach that care will be punished. Voluntary (+) exchange (0) builds trust (-); compelled transfer shrinks it. The rule forces the trade: if you want it, offer something. If I say no, the no stands. The adult’s role is to referee the trade, not to enforce redistribution, so the field remains one worth building on.
Truthfulness at 3 is anchored to the position of maximum attention because the greatest harm comes when a falsehood is told in the spotlight. In that moment, the map bends for everyone. It signals that process is subordinate to performance, that clever cruelty can beat facts if timed well. Truthfulness here isn’t about being “nice”; it is about keeping the reconciliation medium (0) clean so push (+) and resistance (-) can meet without either side being erased. This is also why the penalty for a false report should be small and immediate, not sprawling—so the channel can be trusted again before the day ends.
Male guidance keeps this frame from collapsing at the edges. Boys’ disputes can accelerate from shove to serious harm faster than females can understand or regulate. Someone who has lived with real consequences knows how to read when to assert, when to trade, when to appeal, and when to walk. “Don’t Hit” is not pacifism—it’s ranked moves: first hold (+), then trade (0), then appeal (-), and only fight when safety is in real danger. That hierarchy is learned. Without it, boys either submit and curdle or lash out and escalate. With it, the confidence field and the truth channel survive, and play stays play.
When the threat of real injury is live, male law-setting isn’t about “role” or “tradition,” it’s about credibility in the same evolutionary medium (0) as the potential escalation. In environments where physical risk is absent or minimal, enforcement can shift to whoever holds social authority, because the governing channel (0) is reputational rather than force-based (+).

“The Gambler”
The adult echo of this geometry is in Kenny Rogers’ 1978 hit song The Gambler. The advice is an elder compressing a lifetime of risk management into a handful of rules that keep you solvent in pressure environments. The line “know when to hold ’em, know when to fold ’em” is the neutralizing force in motion—reconciliation as judgment. Hold when your read of the table matches your position; fold when truth to yourself demands you cut loss before it compounds. Both moves protect the bridge between push and resistance.
“Know when to walk away and know when to run” is the affirming force as restraint and as emergency exit. Walking is controlled disengagement; running is full withdrawal when the field has turned lethal. In both cases, escalation is capped before it consumes the table. These are not abstract moves; they are the same judgment calls boys make on playgrounds, in locker rooms, and later in boardrooms and bars. The skill is reading the moment before it becomes irreversible.
“You never count your money when you’re sittin’ at the table” is the denying force in etiquette form. It is a property-rights injunction: don’t seize before the deal is done, and don’t telegraph possession in a way that destabilizes the game. Respect for the property field is what keeps the game playable for everyone. “Every hand’s a winner and every hand’s a loser” is the elder’s truthfulness about uncertainty, spoken at 3 to keep expectations tethered to reality. It strips out the superstition that there’s a way to eliminate risk and keeps the confidence field intact by protecting the process, not the ego.
The closing image of the gambler fading into the dark is a reminder that the advice is not about cards at all. It is about living long enough to keep playing.
The affirming force controls escalation so today’s problem doesn’t become a war. At 3, you keep the signal honest so push and resistance can meet without collapse. At 6, you protect confidence so people will build, trade, and return tomorrow with better tools and stronger commitments. The geometry holds whether you’re six years old in a sandbox or sixty years old at a card table.
This is the first half of the build. Law of Three has given the frame and the seating. Law of Seven will add the kinetics: the unequal steps, the shock points where drift takes over unless you add the right kind of energy, and the two places where verification and closure must be engineered so truth checks don’t kill play and end-of-day doesn’t break trust. For now, the on-ramp is explicit.
The Law of Three is static geometry, unrealized potential — a map of where each universal rule belongs to keep conflict contained and cooperation possible. For a model to work in life, it must survive action. That means testing whether these rules still hold when the sequence is alive, when roles shift, and when the process moves through points of instability. This is where the Law of Seven enters. It takes the fixed positions of the triad and runs them through a repeatable cycle, revealing the shock points where drift begins and the corrective forces that pull the process back on track.
The simplest, most visible way to see this is through a child’s game. Hide-and-Seek may seem lighthearted, but it is a kinetic map of cooperation under minimal enforcement.
The sequence — 1, 2, 4, 5, 7, 8 — is the Law of Seven in motion, with the Three Universal Rules seated as governors at the points of maximum risk. The 132 triad, Concentration, is the correct process for keeping a scene whole under pressure. The three rules make that process visible and testable. Everything else that we add later—rates, shocks, lines—will hang from this without strain.
From Geometry to Motion: Hide-and-Seek
The Law of Seven is process in motion. When the Three Universal Rules are embedded in this sequence, they are no longer abstract principles; they become active governors that keep the process from drifting off course. A perfect demonstration is a round of Hide-and-Seek. At child level, it’s just play. At system level, it’s a live simulation of cooperation under minimal enforcement, running through the sequence 1–2–4–5–7–8.
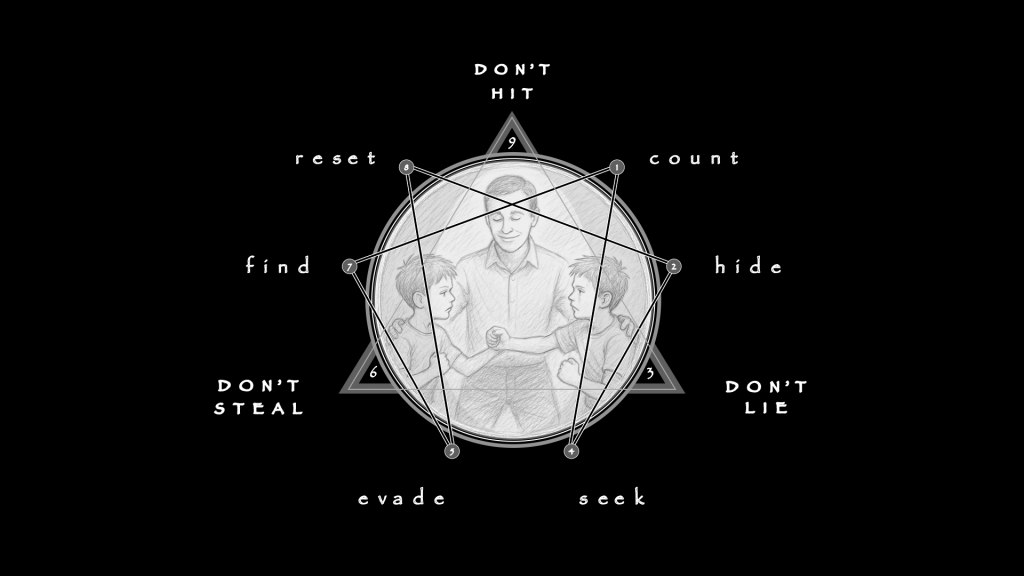
This is a functioning model of a process that cycles through six visible steps before closing the loop. In a single round, these steps are: Count, Hide, Seek, Evade, Find, Reset. Each step is locked by at least one of the Three Universal Rules — Don’t Hit, Don’t Steal, Don’t Lie — and each contains a shock point where the process can drift or collapse if that rule fails.
By placing the rules directly into the sequence, Hide-and-Seek becomes a living diagram of cooperation under constraint. What appears to a child as simple play is, to the trained eye, an early and repeatable demonstration of the same trust mechanics that keep adult systems — markets, negotiations, safety protocols — alive.
Step 1 – Count (Rule: Don’t Lie)
The seeker closes their eyes and counts aloud. This is the first contract of the round. Time is granted for the hiders to disperse. The seeker will not look before the count is finished.
Shock point: If the seeker peeks, they breach the truth channel before the game has properly begun. The breach is not just procedural cheating — it is a corruption of the reconciliation medium, which poisons every later step. Once the perception of honesty is gone, the round cannot be trusted, and later captures are contested whether or not they were fair.
In adult terms, this is the same as falsifying a timestamp, back-dating a contract, or falsifying a safety inspection before the work begins. The process is already broken.
Step 2 – Hide (Rule: Don’t Steal)
Hiders scatter. Each chooses a position within the agreed boundaries. The implicit rule is that once a spot is claimed, it belongs to that player for the round.
Shock point: If a player forces another out of their spot, they steal territory under the guise of “just playing.” The damage is twofold: the displaced player loses their safety, and the game loses its shared definition of fairness. In property-rights terms, this is seizure without compensation. In school, it’s a classmate taking your chair or desk and refusing to move. In sports, it’s a player moving into your assigned position on the field mid-game. In the workplace, it’s a coworker taking your parking spot or workstation without asking. In a startup, this is the competitor who leaks your launch plan before you’ve gone public. In disaster relief, it’s one group occupying the shelter allocated to another, forcing families out into danger.
The adult parallel is obvious. Markets, workplaces, and negotiations collapse into bullying or confiscation when ownership — of resources, roles, or territory — is not respected.
Step 4 – Seek (Rule: Don’t Hit)
The seeker finishes counting, announces the hunt (“Ready or not, here I come!”), and begins searching. This is the first point where physical contact can occur between seeker and hider.
Shock point: Without the “Don’t Hit” rule, a simple tag can escalate into shoving, tripping, or other physical dominance plays — especially in mixed-gender groups where physical capacity varies. In a male–male clash, the escalation risk is higher still: force is part of the evolutionary vocabulary, and without restraint, the game can turn into a fight.
False calls are the drift hazard here. A seeker claiming “I tagged you” when they didn’t, or a hider claiming “I was safe” when they weren’t, destroys the reconciliation bridge between roles. Disputes in this phase often end the round prematurely, just as false reporting in adult contests (financials, scores, deliverables) kills trust in the outcome. In sports, it’s the player claiming a goal or point that never happened. In the workplace, it’s taking credit for someone else’s sale or project completion. In everyday life, it’s cutting in line and insisting you were already there.
Step 5 – Evade (Rule: Don’t Lie)
The hiders’ active phase begins: they stay hidden, shift positions unseen, or dash for base while avoiding capture. The seeker’s active phase is making true captures — tagging a hider before they reach safety.
Shock point: False calls are the drift hazard here. A seeker claiming “I tagged you” when they didn’t, or a hider claiming “I was safe” when they weren’t, destroys the reconciliation bridge between roles. Disputes in this phase often end the round prematurely, just as false reporting in adult contests (financials, scores, deliverables) kills trust in the outcome. In school, it’s the kid insisting “I turned in my homework” when they didn’t. In sports, it’s the player claiming a score that never happened. In the workplace, it’s someone taking credit for a project they didn’t complete. In business, it’s reporting inflated sales figures to impress investors. In politics or public safety, it’s falsely declaring a crisis to trigger resources that aren’t actually needed.
Step 7 – Find (Rules: Don’t Hit / Don’t Steal)
The seeker closes in on the last few hiders. Contact is often closer now, and the safe zone becomes critical. Two rules are active: no physical harm in tagging, and no retroactive theft of safety. If a hider reaches base untagged, the seeker cannot claim them afterward.
Shock point: This is where tempers flare. Fatigue, near-misses, and frustration can lead to bending both force and property rules. In school, it’s shoving a classmate after the teacher calls “time.” In sports, it’s fouling an opponent after the whistle. In the workplace, it’s cutting a colleague out of credit for work already finalized. In business, it’s the last-minute contract rewrite that strips a partner’s agreed share. In politics or diplomacy, it’s moving the goalposts after the other party has already met the stated terms.
Step 8 – Reset (All Three Rules)
The round ends: all hiders are tagged or safe. A new seeker is chosen, and the next cycle begins. For the reset to work, all three rules must hold. No retaliatory hits over grudges from the last round. No stealing of spots or roles in the transition. No lying about what happened at the end.
Shock point: If any of these rules fail here, the loop does not close cleanly. Instead of returning to Step 1, the game collapses into argument, splinter groups, or abandonment. In school, it’s classmates refusing to play another round because of unresolved disputes. In sports, it’s a team refusing a rematch after a controversial call. In the workplace, it’s a project team unwilling to work together again after a messy debrief. In business, it’s partners walking away from future deals after a bad closing experience. In government or diplomacy, it’s failed treaty enforcement that ends cooperation entirely.
The Honor System in Hide-and-Seek
Hide-and-Seek’s entire loop runs on the honor system. There are no referees. Enforcement is light, and violations are often invisible except to the one committing them. The group’s only defense is shared interest in keeping the game alive.
The clearest structural load point is the seeker’s announcement at the end of Step 1: “Ready or not, here I come!” This is the public handshake that certifies the count was honest, the eyes stayed closed, and the hiding phase was protected. It is the moment where the game’s trust reservoir is either replenished or drained.
What makes the honor system here powerful is that the stakes are small enough for children to grasp the cause-and-effect. A cheated round feels bad, and the feeling lingers. A fair round, even if you lose, preserves the willingness to play again. This emotional link between fairness and continuity is what allows trust systems to scale later in life.
This is not sentimental “teaching children values”; it is process engineering via behavioral design. Without public endorsement, however, suspicion creeps in. Players begin cheating back, retaliating, or abandoning the structure altogether. You can see the same pattern play out everyday in high-trust adult enterprises:
- In financial futures markets, the honest close of books at days-end.
- In law, the certification that evidence handling was unbroken.
- In safety operations, the sign-off that protocols were followed before action begins.
In each case, the honor system is not the absence of oversight — it is the presence of mutual survival for the process itself. Cheating can yield a short-term win, but it costs the very field of play.
Hide-and-Seek, then, is not just a children’s pastime. It is a live, repeatable simulation of trust, restraint, and respect for agreed boundaries. By embedding the Three Universal Rules into each point of the sequence, the game becomes a perfect on-ramp for understanding both the geometry of process and the fragile nature of cooperation.
Why This Matters Beyond the Playground
Hide-and-Seek embeds the Three Universal Rules inside a Law of Seven cycle. Each step is an action. Each action has a governing rule. Each rule failure is a shock point.
The honor system is the invisible rail that carries the sequence through those points without derailment. The Universal Rules are the load points; the sequence is the kinetic frame that keeps them alive. Each rule failure has a shock point where drift begins, and each shock point threatens not just the round but the possibility of another round.
In stillness, the Law of Three tells us where the rules belong. In motion, the Law of Seven shows how they are upheld — or lost — under pressure.
The playground renders the child’s world visible. The adult world simply hides the stakes. The Law of One unites them. To a child, unbeknownst, Hide-and-Seek is a load-bearing model of cooperation under minimal enforcement. To an adult observer, it is just a game, albeit one scalable to systems far beyond the schoolyard.
Leave a comment