
Intelligence work exists because people cannot be trusted. Alliances bend, treaties conceal, voices lie. It is not the oldest profession, but it has always been close behind, a shadow industry built on suspicion. Its history is long, mostly untold, and its frontier shifts with every new medium of communication. What survives across centuries is not a set of gadgets or codes but a logic: eyes falling through constriction, glimpses forced into coherence, whispers carried up the chain.
The enneagram frames this better than an ordinary wheel because it is not a list of tasks but a geometry of pressure. It shows why intelligence endures: not to entertain with cinematic climaxes, but to sustain governments and commanders with a steady product. Done right, the work begins with a bang and ends with a whisper — requirements narrowed, fragments reconciled, judgment delivered. The product leaves the office; the cycle resets.
The language of intelligence has always been one of compartments. The shorthand “-INT” is an impersonal way to compress labyrinthine practices into a pair of syllables, allowing tangled bureaucracies and restive coalitions to speak a common tongue. HUMINT refers to human sources, while OSINT signals open sources, and so forth. Though the taxonomy was meant to impose clarity, it’s a potentially poisoned chalice. Experience shows that when categories harden into silos, analysts defend their own turf rather than pursue synthesis. What was designed as scaffolding becomes a prison of jargon. The unsentimental truth here is no secret, that intelligence only achieves force when each of its branches converges and compensates for the weakness of another.
That is why a fundamental non-category must be kept in view from the start. Denial and deception is not a branch but a parasite. It seeps into every stream, corrupting signals with false echoes, staging photographs for imagery analysts, planting rumors in open feeds, and turning human sources into double agents. It does not produce intelligence; it contaminates it.
Lesser sub-branches, from medical to acoustic to battlefield technical exploitation, belong here as well, not because they are unimportant but because they act as overlays rather than stand-alone silos. This is therefore not an entry in the taxonomy but a reminder. Every source can lie, every method can be corrupted. Only when analysts assume the presence of distortion do the true branches function as a living system.
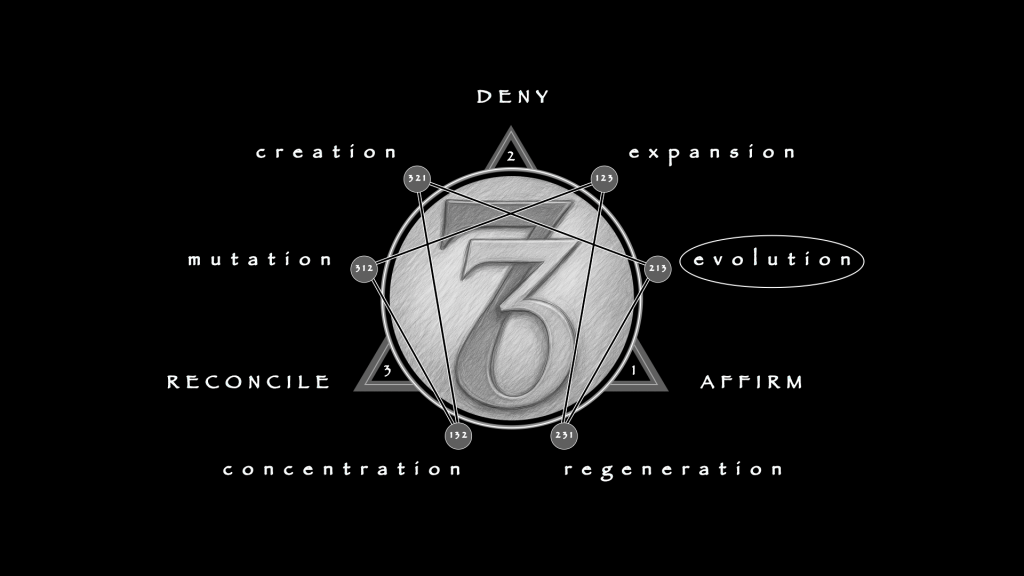
In this 132 triad, strategic imperatives are the affirming force, chance the reconciling hazard, and the product the denying source. 132 is Concentration: to compress fragments into coherence and deliver them upward. Unlike operations that seize ground or ships that move cargo, intelligence itself does not act. It creates a product that prepares action while appearing inert.
The reconciling force enters second as chance. A courier may already be doubled, a photograph staged, a sensor blinded by fog. Hazard bends every stream before it reaches the constriction. The case officer accepts this as law: information degrades the moment it is gathered. What passes through is never pure, always shaped by accident and uncertainty.
The denying force, or source, arrives last as the deliverable. A two-page memo, a single annotated image, a one-sentence cable — all reduce motion to silence. This is why the cinematic image misleads. As always with the enneagram, each node of the Logos triad is literally a point of contact with the real world.
Intelligence does not climax with spectacle. Done right, it begins loud with tasking and channels opened, narrows as fragments are forced into one frame, and ends quiet with a judgment slipped across a desk. The whisper denies the noise that birthed it. The cycle resets. The eyes fall again. Concentration repeats its law.
Most diagrams of the intelligence cycle comprise only five steps. Planning, collection, processing, analysis, dissemination: neat, symmetrical, and false. What gets left out is feedback, the very step that turns error into adaptation. Without it, the model is brittle. It may look efficient on paper, but it cannot correct itself, cannot surface deception, and cannot evolve with tempo. A pentacular wheel is not a living system but a conveyor belt — theoretical production without practical survival.
The enneagram corrects this because it is built on the principle, based on the observable laws of intersecting vibrations, that nothing is missing and nothing is extra. The Six Domains of intelligence work are not arbitrary categories but lawful necessities. Each carries a unique vulnerability that cannot be absorbed by the others. Remove one, and the cycle limps or collapses; add one, and you create redundancy without function. That is why the frame matters. It is not decoration but proof: six and only six organs are needed for the system to breathe.
The test is adversarial. If an enemy can poison a branch without consequence, then the branch was redundant. But in practice each is indispensable. Signals fail at volume, imagery at deception, signatures at cost, open sources at noise, counterintelligence at trust, and humans at fragility. None can be dropped, or substituted. Together they compensate for one another, and together they create a system capable of surviving contact with denial and deception.
This is what distinguishes the enneagram from the pentacular (or worse, the square) wheels that suggest equal steps. The enneagram encodes asymmetry, choke points, and random real-world interference. It is not ritual but practice, a field grammar drawn from how intelligence actually fails. From this frame the Six Domains can be unpacked, each defined by what it delivers, how it fails, and how it is saved by the rest.
SIGINT (+ CYBINT)
Signals intelligence is the nervous system. It was born with radio, matured through satellites, and now saturates networks and cables. It captures not only what is said but the very architecture that carries it. Cyber intelligence extends this reach into routers, protocols, and code, mapping not just messages but the pathways and dependencies between them. In modern practice the two are inseparable: SIGINT listens, CYBINT probes, and together they turn the ether into terrain.
The strength of SIGINT is scale. Entire campaigns can be traced from bursts of chatter or malware signatures spreading through servers. That same scale is also the trap. One week’s intercept can bury an office under terabytes of raw chatter. Human eyes cannot keep pace, so algorithms sift the flood. But automation has blind spots: it misclassifies, overlooks anomalies, and can be gamed by staged traffic. Encryption, rapid rerouting, and false nodes multiply. Adversaries exploit this by seeding false echoes or flooding channels until the signal drowns under noise. The case officer disciplines this chaos by forcing it through six checkpoints — a fixed frame that separates what can be trusted from what is likely poisoned.
- Deliverables: Intercepted communications packages (transcripts, metadata, decrypted content).
- Hazards: Encryption, traffic shaping, and deceptive chatter.
- Counters: Advanced decryption, metadata analysis, and cross-INT corroboration.
- Deliverables: Network and infrastructure maps (command nodes, relays, dependencies).
- Hazards: Proxying, rapid routing changes, and false nodes.
- Counters: Active probing, persistent monitoring, and anomaly correlation.
- Deliverables: Technical alerts (indicators of compromise, anomalous traffic, intrusion signatures).
- Hazards: Polymorphic malware and indicator poisoning flood the system.
- Counters: Behavioral detection, layered threat-hunting, and validation across streams.
SIGINT orients but does not decide. It exposes movement, not motive; traffic, not intent. Alone it is chatter in a void. In the full cycle it is the mapmaker, tracing lines that only gain meaning once the eye, the lab, and the source confirm them.
IMINT (+ GEOINT, PHOTINT)
Imagery is the eye of the system. Where SIGINT hears traffic, IMINT shows its shape. From balloons over the trenches of 1914, to WWII photo-recon runs, to Cold War satellites, and today’s drone feeds, the camera has always promised certainty: here is the facility, here is the convoy, here is the missile on its pad. In 1962, one satellite pass over Cuba turned suspicion into confrontation. The eye can shift history.
But the eye is fragile. Clouds obscure, camouflage deceives, and adversaries know how to stage for the lens. They roll out empty launchers, build mock airframes, seed false geotags, or time movements to pass between scheduled orbits. The gap between looks becomes a weapon. A factory may be only a façade, a parade a screen for hidden weakness. The trap is confidence: images look solid even when they are lies.
Interpretation is the battlefield. Imagery analysts build baselines, detect change, and reconstruct timelines. They fight fatigue, ambiguity, and institutional pressure to “see what leadership wants.” A truck on a highway may be coded as a missile carrier or dismissed as routine logistics; the frame of reference decides which. Every image is a surface that must be tested against law, physics, and other streams before it can be trusted.
- Deliverables: Annotated imagery (facilities, equipment, routes, activities).
- Hazards: Camouflage, decoys, and staged events.
- Counters: Multi-temporal and multi-spectral passes corroborated by other INTs.
- Deliverables: Geospatial overlays (terrain, logistics, infrastructure integration).
- Hazards: Manipulated geotags, misregistration, and falsified overlays.
- Counters: Rigid georeferencing protocols, coordinate cross-checks, and metadata audits.
- Deliverables: Change-detection sequences (before/after comparisons, patterns of life).
- Hazards: Sensor noise, environmental cycles, and staged movements.
- Counters: Multi-sensor confirmation, statistical baselines, and MASINT adjudication.
IMINT rarely stands alone. MASINT adjudicates with spectral signatures, HUMINT adds context from inside the walls. Without them, pictures risk becoming theater. With them, imagery locks signals into place and gives the cycle something solid to carry forward.
IMINT anchors signals and orients planning. Alone it risks illusion. In the cycle it confirms what the ear already suspects.
MASINT (+ ACINT/TECHINT)
Measurement and signature intelligence is the laboratory of the system. Where signals flood and images persuade, MASINT captures what cannot be staged: isotopes drifting in the atmosphere, seismic vibrations in the earth, spectral lines invisible to the eye, the acoustic fingerprint of a submarine. From atmospheric samples after nuclear tests in the 1950s to the acoustic nets strung across oceans in the Cold War, MASINT has always thrived in the margins others could not reach. Acoustic and technical intelligence extend this forensic reach — the hum of a propeller, the dismantling of captured hardware, the recovery of a downed satellite. Together they supply evidence that propaganda cannot fake.
Its strength is authority. A single detection can upend an assessment: an unexpected isotope proves a clandestine test, a tremor locates a launch, an acoustic pattern betrays a submarine’s class. MASINT does not overwhelm with volume; it punctuates with confirmation. Yet authority comes at a cost. A single spectral array may cost more than a squadron of aircraft, yet produce only a handful of decisive detections each year. Specialists are rare, instruments temperamental, and results slow. Adversaries exploit this by cutting emissions, detonating under mountains, or flooding the sea with decoy noise. The danger is not noise but silence — absence of data mistaken for absence of activity.
Interpretation is treacherous. Laboratories fight calibration drift, environmental clutter, and spoofed signals. A tremor may be a test or an earthquake; a plume may be industrial or military. MASINT never looks blind: it follows SIGINT tasking, overlays imagery, and waits for HUMINT to point to a site. It can confirm or demolish a narrative, but it cannot construct one alone.
- Deliverables: Signature libraries (acoustic, spectral, thermal, radiological, seismic baselines).
- Hazards: Emission control and masking disguise true profiles.
- Counters: Expanded libraries, sensor fusion, calibration baselines.
- Deliverables: Event detections (seismic tests, launches, underwater movement).
- Hazards: Spoofed signals or environmental clutter create false or hidden events.
- Counters: Triangulation, multi-modality correlation, forensic discrimination.
- Deliverables: Forensic exploitation of materiel (capabilities, provenance, vulnerabilities).
- Hazards: Tampering, staged recoveries, broken chain-of-custody.
- Counters: Strict custody protocols, lab verification, multi-source corroboration.
MASINT punctuates, not floods. Alone it is too costly and too slow; inside the cycle it bends the narrative with a single verdict.
OSINT (+ FININT)
Open-source intelligence is the floodplain. In WWII, BBC monitoring units sifted radio broadcasts for hidden cues. During the Cold War, intercepted pamphlets and state radio propaganda were read as closely as signals traffic. Today, the flood is digital: news wires, NGO reports, corporate filings, customs records, and above all, social media. Its strength is accessibility: anyone can gather it. Its weakness is that everyone can poison it. Adversaries stage for OSINT precisely because they know it will be watched.
Financial intelligence runs inside this bloodstream. In Prohibition, rum-runners laundered cash through banks; during the Cold War, covert aid moved through front companies; now state actors launder billions through crypto mixers and offshore havens. FININT maps flows of capital as SIGINT maps flows of chatter. It is indispensable for tracing procurement networks, sanction evasion, and covert financing. But money masks itself. Layered transactions, shell structures, and synthetic ledgers leave trails in shadow.
The case officer knows this trap. OSINT overwhelms with volume and velocity; FININT overwhelms with complexity and concealment. Troll farms post identical rumors in dozens of languages. Synthetic videos push staged protests to trending feeds. Thousands of filings conceal the one transaction that matters. The adversary does not need to hide the truth; it only needs to flood you with versions until truth is indistinguishable. The discipline is to assume contamination and prove authenticity through other streams.
- Deliverables: Media and social monitoring (curated feeds, provenance-checked situational awareness).
- Hazards: Disinformation campaigns, bots, synthetic media.
- Counters: Provenance analysis, attribution techniques, human moderation.
- Deliverables: Financial tracing (ownership structures, trade flows, cryptocurrency movement).
- Hazards: Shell companies, mixers, layered transactions.
- Counters: Ledger analysis, trade-data triangulation, institutional cooperation.
- Deliverables: Contextual studies (political, cultural, organizational profiles).
- Hazards: Selective reporting, narrative shaping, cultural traps.
- Counters: Diverse sourcing, native-language expertise, cross-INT validation.
OSINT and FININT provide context no sensor can. But without suspicion they drown the system. Their value is proportional to the rigor of their filters.
Counterintelligence (CI)
Counterintelligence is the immune system. Where other branches collect, CI protects. Its job is survival: to detect infiltrations, expose double agents, shield secrets, and probe for weaknesses before an adversary exploits them. It operates in three modes at once — defensive, offensive, and analytic. Defensively, it vets personnel, audits procedures, and hunts for penetrations. Offensively, it flips agents, runs counter-espionage operations, and feeds deception back to the adversary. Analytically, it maps manipulation, profiles denial-and-deception campaigns, and warns when the cycle itself is being poisoned.
History proves the cost of failure. The Cambridge Five exploited ideological blind spots and crippled British confidence for decades. Hanssen and Ames showed how bureaucracies reward betrayal until it is too late. Each case underscored the same law: once CI falters, every other branch collapses. Signals, images, and sources mean nothing when the adversary is already inside the system.
CI has its own hazards. Its strength is suspicion, but suspicion corrodes. Too little, and penetrations flourish unseen. Too much, and services cannibalize themselves. Adversaries weaponize this by planting whispers, stoking paranoia until an agency burns its own networks. Discipline is what separates vigilance from self-destruction. The FBI’s COINTELPRO is the warning: CI rebranded as political policing, suspicion turned inward on lawful dissent. What was meant to defend the system became the tool that degraded it.
- Deliverables: Threat assessments (penetrations, insider risks, vulnerable compartments).
- Hazards: Long-term infiltrations and subtle influence evade detection.
- Counters: Continuous vetting, behavioral analytics, compartmentation.
- Deliverables: Protective protocols (vetting, auditing, access controls).
- Hazards: Procedural shortcuts, collusion, complacency.
- Counters: Surprise audits, red-team testing, rotation of critical functions.
- Deliverables: Manipulation profiles (adversary denial-and-deception tactics).
- Hazards: Adaptive deception exploits cultural and bureaucratic blind spots.
- Counters: Dynamic playbooks, scenario training, deception-awareness in analysis.
CI shadows every other branch: vetting sources in HUMINT, auditing metadata in SIGINT, checking staging in IMINT. It never delivers a product of its own, but without it nothing delivered can be trusted.
HUMINT
Human intelligence is the heartbeat. Where machines intercept, measure, or image, HUMINT persuades, betrays, and survives. It gains access to places sensors cannot reach: the closed meeting, the private conversation, the intent behind the order. A source may risk his life for a whispered meeting in a café, only to find the handler already under surveillance. No algorithm can replace that risk or the insight it brings.
History shows both its triumphs and failures. During WWII, double agents like GARBO deceived the Axis into misallocating forces on D-Day. Oleg Penkovsky’s reports gave NATO clarity on Soviet capabilities during the Cuban Missile Crisis. Conversely, fabricated defectors in the run-up to the Iraq War poisoned analysis and helped drag nations into conflict. More recently, Taliban infiltrators inside Afghan security forces turned insider access into lethal vulnerability. HUMINT offers clarity when it is true, catastrophe when it is false.
Its hazards are constant. Adversaries seed fabricated defectors, dangle assets, or turn trusted sources into doubles. Handlers misinterpret, press too hard, or believe too quickly. Sources exaggerate, project, or defect. HUMINT requires discipline: rigorous validation, structured debriefs, and continuous cross-checking against other streams. Yet without it, the cycle is blind. Signals reveal traffic, imagery shows movement, signatures confirm events — but only people reveal motive.
- Deliverables: Source reporting (debriefs, insider accounts, observations).
- Hazards: Fabrication, coercion, and doubles seeded by adversaries.
- Counters: Rigorous validation, handler discipline, cross-source corroboration.
- Deliverables: Operational assessments (intent, morale, cohesion, fracture lines).
- Hazards: Spin, projection, and misread signals distort judgment.
- Counters: Structured analytic techniques, triangulation with technical INTs.
- Deliverables: Access opportunities (recruitment pathways, cut-outs, liaison leverage).
- Hazards: Entrapment, counter-recruitment, exposed channels collapse networks.
- Counters: Layered tradecraft, vetted intermediaries, secure cut-out design.
HUMINT validates and is validated. Alone it collapses under lies; in the cycle it gives motive and meaning to every other branch. HUMINT is fragile. HUMINT is decisive. The cycle stops if the heartbeat fails.
Taxonomy is anatomy: six organs, each with a function and a failure. But anatomy without circulation is dead weight. The cycle forces motion, pulling the branches into sequence and testing them under pressure. This is why the common five-spoked wheel is brittle. It leaves feedback out, the pulse that keeps the rest alive. Without it, signals, images, signatures, sources, finances, and suspicion clot into silos. With it, error is surfaced and the loop adapts.
The body may have the right organs, but without circulation they stagnate, and without feedback the pulse flatlines.
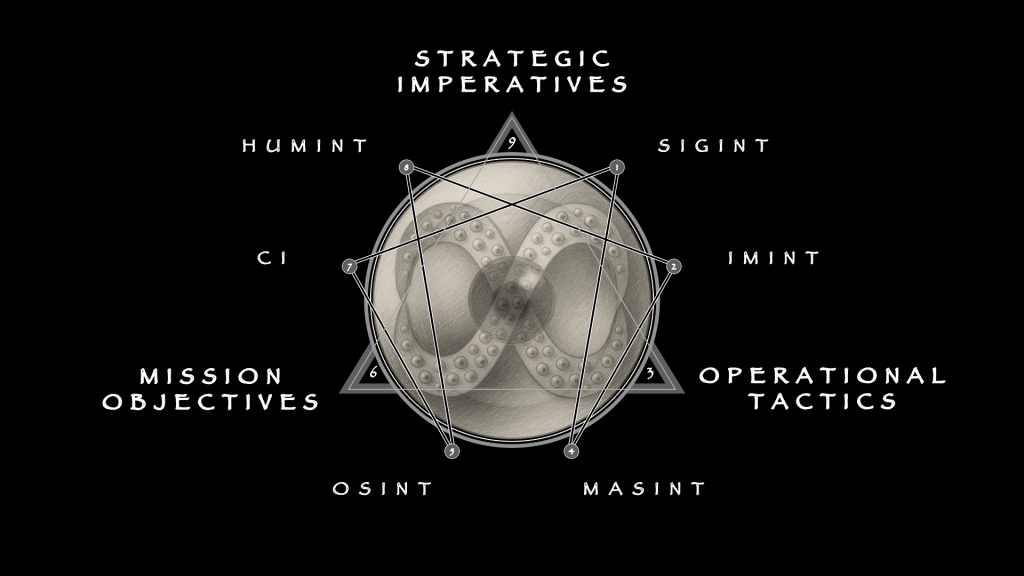
The proof is necessity. Six is not a convenience but a law. Each branch covers a failure no other can absorb. Remove one and the system collapses; add one and you duplicate function. Five is starvation: feedback gone, errors calcified. Seven is inflation: padded categories that create paperwork but no survival. Six is survival — nothing missing, nothing extra.
Consider what happens when one organ is skipped. Neglect SIGINT and chatter moves unseen. Neglect IMINT and movements are guessed instead of seen. Neglect MASINT and deception thrives in the lab. Neglect OSINT and context collapses. Neglect CI and infiltration festers. Neglect HUMINT and intent vanishes. The adversary presses hardest at the missing station, turning silence into leverage. The geometry in the Six Domains exhibit guarantees coverage: all present, none redundant.
The body may have the right organs, but organs alone rot without circulation. They need rhythm. They need pulse, and oxygen. They need shock at the moments where law says drift will appear. This is where the second frame, Diagnostics, sharpens the point: the cycle survives not just by having parts, but by testing them relentlessly.

Each station doubles as an interrogative. At planning, assumptions must be broken open. At direction, scope must be calibrated or glut overwhelms. At mid-cycle, chance and circumstance intrude — random breaks and local density both distort. At contact, adversarial moves must be confronted, not wished away. At closure, systemic links must be drawn, or findings fragment into trivia. Skip one check and the cycle is already poisoned. Taken together, the inform the case officer’s Six Questions.
The adversary does not need to win everywhere. It needs only one missed test: one assumption left unchallenged, one scope drawn too narrow, one chance event dismissed, one deception unexamined. Drift hides exactly where the case officer looks away.
Intelligence breathes only in sequence. Planning, collection, processing, analysis, dissemination, feedback — Six Crafts, each one both function and failure point. They do not move in equal stride. Some race, others choke. Planning risks starvation if scoped too narrow, or glut if too broad. Collection floods the system or runs dry. Processing buries the signal under trivia. Analysis collapses into bias. Dissemination bottlenecks in silos. Feedback is dismissed, and error calcifies. Each is provisional, contested, and indispensable.
This is a genuine difference between other flowcharts and the enneagram. Most sell smooth arcs, an illusion of equal steps. The enneagram maps asymmetry, shock points, and drift. It predicts where effort will stall and where denial and deception will press hardest. Adversaries seed false requirements at planning, flood collection with noise, tamper with processing metadata, exploit bias in analysis, intercept dissemination channels, and suppress feedback. The geometry shows that these pressures are not accidents; they are the lawful places where cycles break.
Taxonomy names the Six Domains. Diagnostics reveals the traps. The cycle outlines tradecraft in the field. From here the forms move, and functions are tested in sequence.

Processing orders the flood but does not decide its meaning. Transcripts, annotated images, graphs, ledgers — still fragments. If processing stalls, noise buries the cycle. If it works, the fragments reach the stage where judgment begins.
Processing sorts. Analysis judges. Here error deepens. Analysts confirm what they believe, mirror their own assumptions, or collapse into consensus. Adversaries exploit this, feeding signals and stories that match expectation. The costliest failures in intelligence come not from missing data but from misreading it.
Diagnostics marks this in bold. Assumptions must be broken, competing models forced against each other, and bias exposed. Skip the test and deception holds.
Plan and Direct
Planning and direction are the gateway to the cycle, but they are also the first shock point. Under the Law of Seven this is the mi→fa gap — a stage that demands reconciling force or the process drifts before it starts. The cycle is proactive, focused, but not yet acting. It frames requirements and sets boundaries, producing the conditions for work without doing the work itself.
The planner’s craft is calibration. Scope too narrow starves; too broad drowns. Each branch bends planning: OSINT widens toward visible noise; HUMINT tempts with rumor and nuance; CI injects suspicion, asking whether the question itself has been planted. Even here, the adversary presses the 2⟶8 axis, trying to warp strategic imperatives into poisoned objectives. Planning is not neutral; it is contested terrain.
The quadratic arc clarifies the weight. At point 1, spark condenses; at point 4, it enters the corridor; planning is that release of potential energy, the drop that sets the cycle into motion. If the release is crooked, every subsequent move is bent. History shows this: Israeli requirements before Yom Kippur built on the “Concept” that Egypt would not attack; U.S. planning before Iraq in 2003 framed the search for WMD as an axiom. In both cases, intelligence was present in abundance, but the frame was poisoned at the start.
- Which assumption blinds us before collection even begins?
- Is our scope tight enough to focus yet wide enough to catch surprise?
- Where are incentives pushing us to lie to ourselves about requirements?
- What flex keeps today’s plan bending without breaking?
- If I were the adversary, how would I plant this very question?
- How will this frame distort the next cycle when tempo compresses?
Good planning accepts imperfection and builds flex. Requirements are provisional hypotheses, not dogma. Rescope as context shifts. Submit the frame to continuous CI review, or the system marches forward carrying a poisoned seed. Planning is not simply the beginning; it is the place where the entire cycle can already be lost.
Collect
Collection begins where planning leaves off. Requirements framed, the system turns outward, gathering raw material through every available channel. It does not act on the adversary; it concentrates fragments into the system, drawing them into shape. Energy released in planning drops into the corridor of collection (the 1⟶4 line) where potential becomes flow.
Each branch feeds this station. Signals are intercepted from radio chatter, fiber-optic cables, or compromised servers. Images captured by satellites and drones, coordinates tagged. Measurements logged from vibrations, isotopes, acoustic signatures. Open sources and financial records scraped, both genuine and staged. CI probes for penetrations. HUMINT supplies reports from denied spaces. Appetite is energy, but appetite carries risk.
The first danger is imbalance. Overreliance on one stream distorts. Lean on SIGINT and drown in chatter while missing intent. Trust IMINT and be dazzled by parades while blind to stockpiles. Neglect MASINT and deception thrives in the lab. Overweight OSINT and context drowns precision. Each skipped channel is a gap the adversary exploits. Diversification is essential, but glut itself is crippling. Scarcity and glut are not opposites here — they are twin hazards.
History proves the point. In WWII, bad weather blinded Allied bombers when aerial reconnaissance failed. In 1991, Iraqi forces staged decoy tanks and artillery to bait collection into waste. The adversary presses hardest here, seeding false communications, staging parades for sensors, planting doctored financials, flooding social feeds with counterfeit narratives. Collection is the system’s widest gate, and openness is vulnerability: everything enters, including poison.
- Which stream do we trust too much without proof?
- How balanced is our intake — leaning on chatter, images, or rumor?
- Where is chance entering as poison — signals staged, sources turned, records doctored?
- What redundancies ensure one rotten channel cannot set the picture?
- If I were the adversary, how would I flood or starve this office’s collectors?
- How will today’s imbalance cripple tomorrow’s processing when tempo accelerates?
The best practice is not purity but resilience. Streams must be cross-validated. Redundancy is not waste — it is survival. Only convergence builds confidence. Collection must also be time-sensitive: stale data misleads as effectively as false data. The discipline is to move quickly without cutting corners, to accept imperfection while denying single-point failure. Without that, collection collapses into accumulation, and the system mistakes volume for value. Collection is not knowing more. It is knowing enough to survive distortion.
Process
Processing is the chokepoint of the cycle. Once the flood of fragments is drawn in, the system must sort, tag, translate, and archive or it drowns in its own appetite. Collection is voracious; processing is selective. Here the system risks paralysis.
The work is backstage but decisive. Signals become transcripts, imagery annotated files, measurements graphs, financial records ledgers. Raw fragments gain form, but not yet meaning. If processing fails, analysis never begins. If it succeeds, it passes a structured current forward, stripped of noise but still provisional.
The hazard is overload. Automation promises relief, but algorithms carry blind spots — missing anomalies, mistaking noise for signal, or being gamed by adversaries who know the filters. Human analysts bring intuition, but also fatigue, bias, and error. The adversary exploits both: flooding channels to overwhelm, crafting metadata to mislead, or tampering with chain-of-custody so the poisoned fragment becomes authoritative. The system risks collapsing not from absence but from excess.
History repeats the warning. In Vietnam, signals traffic flooded processing centers faster than it could be translated, burying decisive intelligence under chatter. In more recent cyber conflicts, adversaries have seeded indicator lists with false signatures, ensuring that defensive systems misclassified benign traffic as hostile and ignored the real intrusions. Processing is where error multiplies if filters fail.
- What criteria decide what is filtered, and who set them?
- Are we sorting to clarity or only piling into archives?
- Where will noise bury the signal until it is lost?
- What triage method preserves signal without paralysis?
- If I were the adversary, how would I exploit our fatigue or automation bias here?
- How will today’s misclassification warp tomorrow’s analysis under time pressure?
The best practice is ruthless triage joined to transparency. Not all data can be saved; what is kept must be traceable. Metadata must support retrieval, not entombment. Automation must be checked by human judgment, and human judgment must be disciplined by review. Without that balance, processing becomes the graveyard of intelligence.
Analyze
Analysis is the waist of the hourglass — the choke where fragments must collapse into one frame. Here intelligence stops counting and starts deciding what the fragments mean. Links between actors, shifts in behavior, risks and opportunities emerge — or are fabricated. This is the most human stage and, therefore, the most fragile. Machines can process; only people can ascribe meaning. And meaning is exactly where deception cuts deepest.
Each branch lands differently on the analyst’s desk. SIGINT gives tempo and network shape but not intent. IMINT anchors events to place and time yet tempts with theater. MASINT adjudicates with hard signatures, late but decisive. OSINT floods with narrative, the easiest channel to poison. HUMINT supplies motive and mood — decisive when true, catastrophic when false. CI shadows the lot, probing assumptions and seeding red-team narratives so consensus fractures before it calcifies.
Bias is the standing hazard; adversaries weaponize it. Confirmation and mirror-imaging make comfortable stories feel true. Groupthink and tempo pressure reward neat answers over correct ones. Deception campaigns exploit this by feeding exactly the story expected, complete with “truthy” detail to pass a cursory check. Chance itself intrudes here, with coincidences mistaken for causation and anomalies overfitted into proof. Provenance chains are the discipline: without clear lineage from collection through processing, analysts argue stories rather than evidence.
- Which assumption is already blinding us?
- What competing models also fit these data, and why did we favor this one?
- Where has chance or staged coincidence seduced us into “truthy” certainty?
- What dissent or red-team is cutting across our preferred narrative?
- If I were the adversary, what story would I craft to make us confident and wrong?
- How will this judgment survive dissemination deadlines and policymaker tempo?
Safeguards are adversarial method and iteration. Force model competition, preserve provenance, institutionalize dissent. Treat conclusions as conditional and spend confidence only as verification arrives. Analysis fails loudest when it feels most certain — and certainty is the adversary’s most effective weapon.
Disseminate
Dissemination is the handoff — the point where intelligence leaves the analyst’s desk and enters the bloodstream of decision. A judgment not delivered in usable form is dead weight, no matter how correct. This stage appears straightforward — reports, briefings, images, alerts — but it is riddled with failure points. Speed, format, and channel matter as much as content. Delivered too late, intelligence is irrelevant; delivered too raw, it overwhelms; delivered in the wrong form, it is ignored.
Branches demand different treatment. Imagery lends itself to visuals but risks oversimplification. HUMINT requires narrative with nuance, or it distorts. Signals and measurements demand translation into non-technical language, or they remain opaque. Dissemination is therefore not neutral delivery but active shaping, where every choice about format and emphasis decides whether the product is acted upon or shelved.
History shows the stakes. During the Cuban Missile Crisis, annotated photographs reached Kennedy within hours, compressing the cycle to match tempo. In contrast, the Iraq WMD estimates of 2002 were not only flawed in content but poisoned in delivery — presented with unjustified certainty that foreclosed dissent. In both cases, dissemination was decisive: speed with shape versus distortion at tempo.
Here denial and deception strike hard. Adversaries intercept channels, leak selectively, manipulate formats, or bury genuine assessments under bureaucratic avalanche. Internal sabotage is just as common: silos hoard, rivalries delay, clearance walls block the flow. CI belongs here too, not only guarding against compromise but testing delivery channels for resilience under stress. The cycle that survived bias and overload can still fail at the final mile.
- Who actually needs this product, and how must it be shaped to act?
- Are we delivering clarity, or drowning decision-makers in detail?
- Where will chance strike — delay, garbling, leaks, or distortion?
- What protections ensure speed, security, and adaptation in the channel?
- If I were the adversary, how would I compromise or discredit this report?
- How will bottlenecks here choke the feedback loop and poison the next cycle?
Best practice is speed with shape. Products must move swiftly and securely, tailored to audience without diluting substance. Dissemination sits on the downward arc of the system: potential turning into action. At this stage tempo is everything. A perfect assessment delivered late is not intelligence. It is failure.
Feedback
Feedback is the closing turn of the cycle, but it is not closure. On the 7→1 line it masquerades as an ending, a reset to planning, when in truth it is momentum transfer — the energy of error carried forward under a new name. Without it, mistakes calcify and the cycle stiffens into ritual. With it, distortion is recycled into adaptation.
The hazard is neglect. Feedback is dismissed as bureaucracy, or suppressed because it admits failure. Institutions resist correction, so they rehearse error as if it were process. The adversary exploits this by tampering with after-action reports, planting false critiques, or letting silence itself become the poison — no complaint mistaken for validation. On the 2–8 axis, this is where tactical failure can be converted into strategic adaptation. If the loop closes cleanly, lessons learned at the field edge feed imperatives at the top. If it fails, the axis collapses, and tomorrow’s objectives are distorted before they are even named.
History makes the geometry plain. After Pearl Harbor, postmortems exposed systemic blind spots, but without true feedback the same failures reappeared in Korea. By contrast, the post-9/11 counterterrorism centers built rapid loops into their design, imperfect but adaptive, bending planning in near-real time. One cycle repeated error; the other recycled error into change.
Feedback is tempo-bound. A lesson delivered months later is trivia. A lesson delivered within hours can bend requirements before they lock. CI belongs here too, probing whether adversaries are shaping critiques or whether leaders are filtering out the most dangerous truths.
- Who is telling us the truth about our product, and who is just nodding?
- Are the same errors repeating because pride resists correction?
- Where is chance hiding — false after-action, buried critique, silence mistaken for success?
- What loop forces learning fast enough to matter before the next cycle?
- If I were the adversary, how would I exploit reluctance to admit failure?
- How will today’s neglected feedback distort tomorrow’s planning under pressure?
Best practice is to institutionalize critique, enforce tempo, and protect the loop itself from compromise. Feedback is not the end of intelligence. It is the system listening to itself under pressure — and deciding whether survival comes through repetition or adaptation.
The cycle plays out as 132, Concentration. Every stage up to now has carried that logic: gathering fragments, shaping them into product, delivering judgment but not execution. Concentration sustains governments and commanders by keeping intelligence flowing upward, neither heroic nor climactic, but steady.
The handoff comes here, at the point where the cycle has been walked in full and must now be interpreted through its deeper geometry.

That geometry is 231, Evolution. Concentration explains practice; Evolution explains survival. Concentration makes a product; Evolution adapts under distortion.
The pivot is necessary because intelligence is never a closed loop. Planning does not simply open the cycle; it is already bent by hazard. Japanese deception broadcasts in 1942 prove the point. Analysts chased phantom fleets because planning leaned too heavily on signals. SIGINT offered maps of who spoke, how often, and at what tempo, but adversaries shaped those maps by seeding false echoes and leaving channels open as bait.
In the cyber era, CYBINT multiplies the reach into routers, cables, and protocols, but it magnifies the fragility. Malware can be planted to be discovered; chatter can be staged to look authentic. Concentration frames signals as orientation; Evolution forces calibration. Requirements must be provisional, constantly tested across branches, subjected to CI review from the start. The lesson is clear: Concentration makes intelligence a product, but Evolution keeps it alive under contest.
Imagery shows how that contest expands. The Cuban photographs of 1962 turned confrontation into crisis by anchoring rumor to frames. Yet clouds obscure, camouflage deceives, parades create theater. A truck in a photograph may be a missile carrier or an empty shell. Evolution treats imagery as mutation, each frame provisional, tested against others, sequenced over time. Adversaries build mock-ups because they know the eye is hungry for closure.
Evolution disciplines the eye by forcing diversity—multi-angle, multi-temporal, multi-source—so that no single shot becomes gospel.
Measurement and processing drive the point further. Nuclear tests are confirmed not by photographs but by isotopes drifting in the atmosphere. A spectral line or seismic tremor cannot be staged with ease. Yet signatures are costly and buried in glut. Processing must discard as much as it preserves, or the system collapses under noise. Adversaries exploit fatigue and algorithmic bias, flooding metadata until paralysis sets in. Evolution demands transparent filters and ruthless triage: every fragment traced, every discard acknowledged, the system mutating instead of choking.
Open sources carry the same hazard. Corporate filings, social movements, and financial trails reveal intent early, yet they are also the easiest to manipulate. The Iraq WMD narrative was not just a failure of classified streams but of open ones, shaped by adversary spin and domestic appetite. Evolution resists by adversarial method. Competing models must be forced against the same data. Red-teaming and dissent keep analysis mutating instead of ossifying into consensus. Chance appears here as “truthy” detail; Evolution answers with iteration, never finality. Certainty is collapse; adaptation is survival.
Dissemination and counterintelligence show how survival depends on transfer. Venona decrypts mattered only when they reached policymakers in usable form. The Iraq estimate poisoned decision-making because delivery was framed as certainty. Adversaries need not block delivery outright; slowing it, leaking selectively, or bending format is enough. Internally, silos and rivalries do the rest. Evolution forces speed with shape: clarity tailored to audience, secured against compromise, moving fast enough to act. CI shadows the process, testing whether the channel has been bent. A perfect assessment delivered late is an epitaph.
Feedback reveals the illusion of closure. On the 7⟶1 line it looks like reset, but in Evolution it is momentum transfer, error carried forward under a new name. HUMINT mirrors this fragility: the source inside a denied space is provisional, fallible, always contested. Pearl Harbor and Korea proved that after-action without feedback is ritual; post-9/11 fusion centers, however imperfect, forced adaptation at tempo. Adversaries exploit reluctance by burying critique or letting silence itself become validation. Evolution here is the system mutating itself, interrogating its own product, correcting in cycle-time rather than decades. Without it, intelligence repeats mistakes under the illusion of process. With it, the organism survives distortion.
Symmetry is not stability; it is tension. The cycle does not hold because its six parts are secure; it holds because its six parts are contested. Chance and circumstance are the permanent poles of that contest. The field agent feels chance as danger: every signal may be a trap, every photograph a stage, every source a double. Circumstance, at the field level, looks like luck: the meeting that does not go wrong, the random intercept that saves a life. But the office cannot rely on luck. At the systemic level, chance is permanent and circumstance must be engineered. Redundancy, cross-validation, and feedback loops are designed circumstance, capacity to bend without breaking.
The sixfold cycle holds this tension in each stage. Planning is bent by planted requirements; circumstance insists on provisional scoping. Collection is flooded by deception; circumstance diversifies streams. Processing is overwhelmed by noise; circumstance disciplines triage. Analysis is seduced by bias; circumstance enforces dissent. Dissemination is sabotaged by tempo; circumstance secures clarity and speed. Feedback is poisoned by silence; circumstance forces error into correction.
Here the 3⟶6 line, the sole horizontal axis, reveals itself. Chance is inevitable: distortion, deception, failure. Circumstance is the possibility of “failing forward”: adaptation, engineered survival. The fulcrum of the geometry is not stability but surrender and recovery, loss metabolized into gain. This is the 231 triad, Evolution, in its purest form—not a wheel repeating, but a system mutating forward.
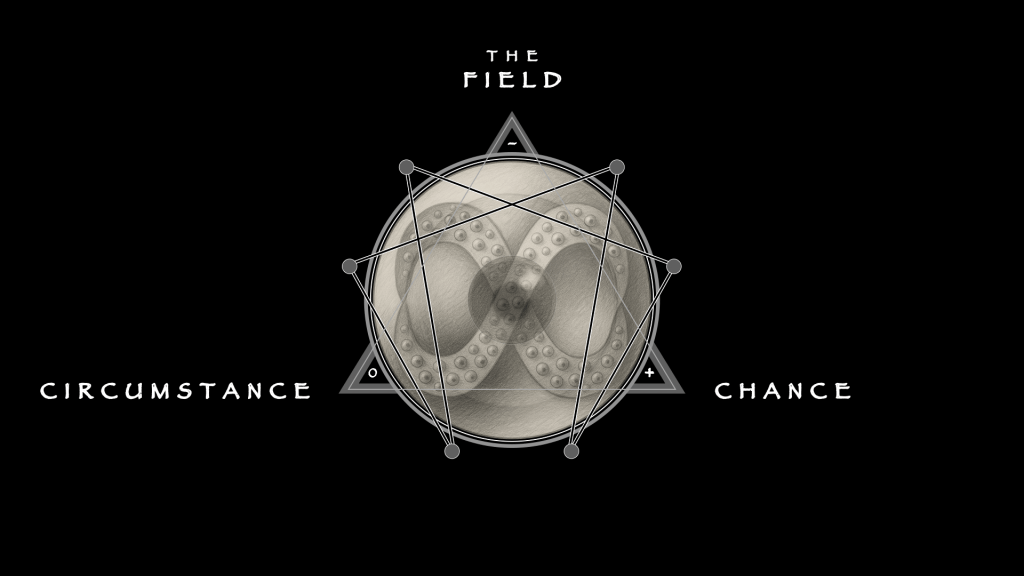
Fragility itself can be organized. Intelligence survives and prospers not by eliminating hazard but by metabolizing it. Chance without circumstance paralyzes. Circumstance without chance breeds complacency. Held together, they generate the tensegrity that makes the system real. Intelligence is not certainty. It is not perfection. It is adaptation—a geometry that survives distortion because it expects it, bends to it, and keeps moving. The geometry endures because tension endures: fragility organized into function.
Leave a comment