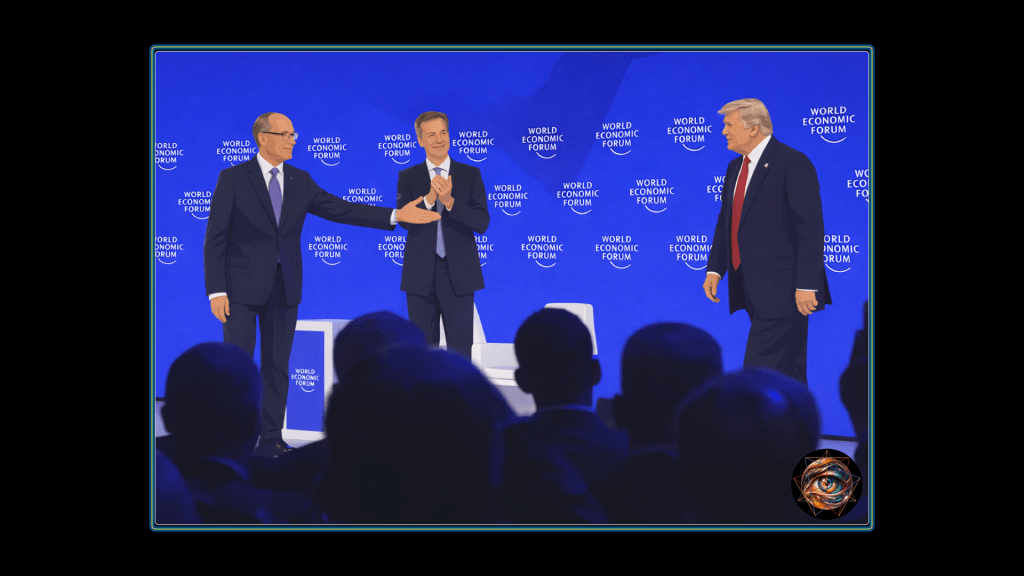
“A very smart man called me daddy,” Trump told the room. “He said, ‘He’s our daddy. He’s running it.’” The president of the United States stood before the World Economic Forum recounting this tribute with undisguised satisfaction, describing his role as patriarch of the NATO alliance to an audience of executives, central bankers, and heads of state who understood they were being informed of their place in the hierarchy. The Americans watching at home saw validation: their president commanding respect, extracting acknowledgment of American indispensability from global elites. The people in the chairs saw something else entirely.
They saw a man describing his leverage over them while they sat in seats they had paid handsomely to occupy. They saw threats dressed as grievances, demands framed as observations, and an ultimatum structure so consistent across topics that its pattern became unmistakable before the first hour concluded. They also saw the gap between the claims being made and the reality they knew from their own data, their own deals, their own participation in constructing the announcements Trump was citing as evidence of triumph.
The World Economic Forum has always trafficked in a particular fiction, the notion that global capital and national power can find common language in the Alpine air. Trump’s address stripped that fiction bare, replacing it with a simpler proposition: America holds leverage, and the invoice is now due. The information asymmetry between the television audience and the live audience was not incidental to the performance. It was the performance, and everyone in the room understood this except, perhaps, the performer himself.
Trump’s seventy-minute address covered six domains where his claims and the room’s knowledge diverged, each domain requiring greater complexity of execution than the last. The progression reveals where American leverage operates without constraint, where it encounters friction, and where it generates adaptive responses that limit future leverage across all domains. What emerged was a hypothesis about American power: that economic, military, and diplomatic weight can extract concessions from allies and adversaries simultaneously while maintaining the prosperity that makes extraction sustainable. The evidence assembled in that room suggested where the hypothesis holds, where it requires qualification, and where it fails tests that sophisticated observers recognized immediately and domestic audiences may not discover until the invoice arrives.
The Machinery of Reduction
Workforce and deregulation as baseline achievement
The federal workforce reduction demonstrates what Trump’s framework accomplishes when execution depends on nothing beyond executive will. No foreign government must comply. No private capital must flow. No counterparty must accept terms. The president signs orders, agencies implement, employees depart. Pure leverage, requiring no negotiation and facing no external limit.
The numbers need no inflation because reality speaks for itself. Federal agencies shed over 322,000 employees since Trump’s inauguration, with departures outpacing new hires by more than three to one. Schedule F implementation on day one reclassified 50,000 federal employees into positions vulnerable to rapid removal, and the promised 10:1 deregulation ratio was not merely met but exceeded by an order of magnitude: 646 deregulatory actions against 5 new regulations in fiscal 2025, a ratio of 129:1 that transformed the regulatory landscape more dramatically than any calendar year on record. The administration achieved precisely what it promised, at precisely the pace it promised, with precisely the instruments it identified. The machinery ground through bureaucratic resistance with relentlessness that only sustained executive commitment can produce, and the grinding continues.
The savings breakdown reveals where deregulation creates value and for whom:
- FinCEN beneficial ownership disclosure rollback: $128.6 billion
- Medicare staffing standards reversal: $55.1 billion
- Remaining deregulatory actions: $28.1 billion
For American audiences, this reads as promise kept. The administrative state is shrinking, regulatory friction falling, government employment declining at a pace not seen since World War II demobilization. The domestic message emphasizes liberation: businesses operating without federal interference, savings flowing to productive investment rather than compliance bureaucracy. Trump delivered this narrative with the confidence of a man presenting evidence that requires no defense, because on this topic, it required none.
The international audience performed different calculations. Deregulation does not eliminate risk; it relocates risk from regulated entities to workers, consumers, and counterparties. The beneficial ownership rollback means reduced transparency in corporate structures, complicating due diligence for European firms accustomed to knowing their American partners. Medicare staffing reversals mean different operating conditions for healthcare investments, different liability exposures, different workforce assumptions. European capital, shaped by regulatory environments treating stability as feature rather than obstacle, must now price American volatility into every cross-border decision. The machinery works precisely as advertised, but machines are neutral regarding who gets caught in the gears.
The Energy Advantage
Production expansion as leverage foundation
Trump’s energy claims rest on firmer ground than his broader assertions because American geology created advantages that policy accelerates but did not invent. The shale formations, the pipeline infrastructure, the skilled extraction workforce accumulated over decades: these assets predate Trump and will outlast him. His administration removed obstacles that previous policy had erected, allowing natural advantages to express themselves in production figures and pump prices that connect to household budgets in ways abstract indicators cannot match.
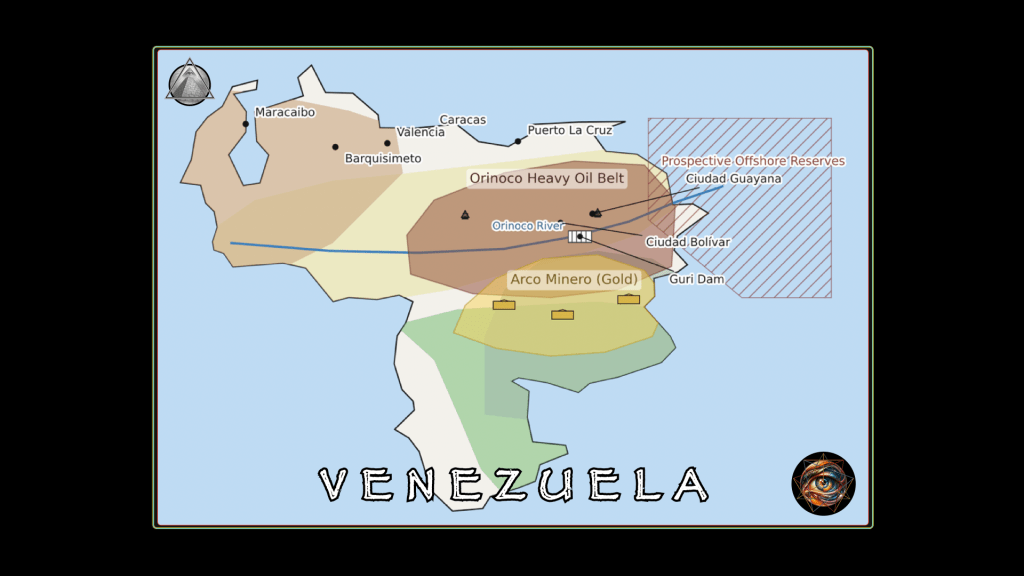
Natural gas production reached all-time highs. Oil output increased by 730,000 barrels per day. Venezuela added 50 million barrels to American-controlled supply, with Trump noting that “every major oil company is coming in with us” on development. Gasoline fell below $2.50 per gallon in many states, with some locations reporting $1.95, figures Americans experience as direct policy validation every time they fill their tanks. The contrast with Biden-era prices above $5 per gallon needs no elaboration; the pump displays the argument more effectively than any speech could.
For domestic audiences, Trump framed this abundance as common sense triumphant over ideological obstruction, prosperity that was always available but locked behind regulations serving environmental pieties rather than working families. He cited the 95% reduction in new domestic oil and gas leases under Biden as evidence of deliberate suppression, positioning his approach as restoration rather than innovation. The narrative resonates because it contains enough truth to survive casual examination: restrictions removed, production increased, prices fell, sequence implying causation that voters experience at the gas station weekly.
The room received the energy discussion differently, because Trump devoted substantial time to mocking European policy with evident relish. Germany generates 22% less electricity than in 2017. The United Kingdom produces one-third of the energy it did in 1999 while sitting atop the North Sea, “one of the greatest reserves anywhere in the world.” Windmills came in for particular ridicule: “The more windmills a country has, the more money that country loses.” China manufactures them and sells them “to the stupid people that buy them, but they don’t use them themselves,” erecting display farms that “don’t spin, don’t do anything” while burning coal for actual power.
The mockery was the message. American energy abundance is not merely domestic success but the foundation for leverage across every other domain. Europe’s vulnerability after Russian supply disruptions means European leaders approach trade, defense, and territorial discussions from structural weakness. Trump controls a resource his counterparties desperately need, transforming every bilateral negotiation into a conversation where one party holds cards the other cannot match. The executives and ministers absorbing this understood they were being told their position, not invited to discuss it.

The Tariff Arithmetic
Trade claims and the selective statistics of victory
Trump announced that his administration had “slashed our monthly trade deficit by a staggering 77%,” a figure designed to sound like transformation. The October 2025 deficit did fall to $29.4 billion, the lowest since June 2009. Tariff revenue reached $236 billion through November, real money from importers who passed costs to consumers but whose payments nonetheless demonstrated policy achieving its stated mechanism. The numbers were not fabricated. They were selected, and selection is its own form of construction.
Domestic audiences heard national restoration, the narrative Trump has refined across three campaigns and now delivers with practiced fluency. Foreign nations finally “paying for the damage they’ve caused.” Steel production increasing, factory construction up 41%, car plants returning from Mexico and Canada. The manufacturing narrative finds apparent confirmation in visible facilities rather than abstract statistics, in groundbreakings and ribbon cuttings that local news covers and national news aggregates into a mosaic of revival. Trump positioned tariffs as instruments of justice that predecessors lacked courage to deploy, as the obvious policy that obvious cowardice had prevented, now implemented by a leader unafraid of the howling from those who preferred the old arrangements.
The room applied context Trump omitted. The full-year 2025 goods deficit still exceeded $1 trillion, inflated by front-loading as companies stockpiled inventory before tariffs hit. Economists from the Committee for a Responsible Federal Budget noted that progress has been “layered on top of an early-year import surge” making year-end assessment genuinely difficult. The 77% figure represents a snapshot within a volatile year, not stable equilibrium. Manufacturing employment actually declined in 2025 despite tariff implementation, the reshoring story requiring workers on factory floors who have not yet materialized. The Peterson Institute calculated U.S. tariff rates on Chinese goods reaching 47.5%, yet uncertainty has discouraged investment in many sectors rather than spurring the renaissance Trump described.
Trump’s anecdotes revealed his method with uncomfortable clarity. He raised Swiss tariffs from 30% to 39% because the prime minister “rubbed me the wrong way,” a detail shared with evident pride. Emmanuel Macron received similar treatment on pharmaceuticals: demand, refusal, threat escalation, compliance. “No, no, no, Donald, I will not do it,” Trump recalled Macron saying, before the tariff threat produced capitulation in what Trump claimed averaged “three minutes a country.” The arithmetic works when counterparties value American market access more than compliance costs, but personalization introduces volatility that makes long-term planning impossible. European discussions of alternative partnerships have intensified precisely because the current arrangement depends on one man’s mood. The room could calculate that dependency, even if the television audience could not.
The Investment Mirage
The gap between announcement and capital formation
Trump’s assertion of “$18 trillion, possibly $20 trillion” in investment commitments represents the speech’s largest departure from verifiable reality. The figure sounds transformative because it exceeds anything any country has achieved, a point Trump emphasized repeatedly, positioning America as the destination for global capital fleeing uncertainty elsewhere. The domestic audience received an impression of sophisticated allocators validating American policy through allocation decisions, the world’s smartest money voting with trillions in a confidence referendum Trump had won decisively. The narrative suggests that capital knows something voters sense but cannot prove, that the investment surge confirms what the election expressed.
The room knew otherwise, because many of them had constructed the announcements being cited.
Bloomberg Economics analyzed the 137 projects on the White House website and identified approximately $7 trillion in plausibly real investment pledges. The gap between $7 trillion and $20 trillion represents different categories bundled for political effect:
- Qatar’s $1.2 trillion: “economic exchange” commitment, not direct investment
- India’s $500 billion: bilateral trade target for 2030, not capital formation
- Apple’s $600 billion: repackaged existing supplier spending, data centers, facilities
- Government commitments totaling $2.27 trillion: mostly vague purchase promises
Actual measured foreign direct investment from January to October 2025 reached $270 billion, more than double Biden-era pace but far below the $1.2 trillion annually Trump’s figures would require. Federal data shows corporate investment levels in 2025 remaining roughly in line with 2024, companies on track to invest over $5 trillion annually consistent with historical trends rather than transformative surge. The Peterson Institute projected $400 billion for full-year 2025, a strong number bearing no resemblance to the multiple trillions described.
The mirage shimmered convincingly for viewers at distance. The executives who had negotiated the Qatar exchange, who had structured Apple’s repackaging, understood exactly what those commitments contained and what they did not. They watched Trump present their hedged arrangements as unprecedented capital flows, knowing the domestic audience lacked context to recognize the gap between appearance and substance. Information asymmetry reached its peak in this room on this topic, because the people who built the illusion sat watching it projected for audiences who would never see behind the screen. The screen is all most viewers will ever see, and on the screen, $20 trillion looks exactly like $20 trillion.

The Alliance Ledger
NATO contributions and the degradation of credibility
Trump’s NATO discussion moved into territory where both audiences understood stakes but diverged on interpretation. American military power underwrites European security; cost distribution has generated friction for decades. The domestic audience heard overdue correction of freeloading. The international audience heard conditional commitment from a guarantor whose conditions keep escalating, whose reliability now depends on continuous payment of tribute whose amount the guarantor alone determines.
Trump claimed credit for moving NATO spending from 2% to 5% of GDP, quoting the “daddy” designation with satisfaction that suggested he understood exactly what the epithet implied about the relationship. The factual record supports American pressure as contributing factor: at the June 2025 Hague summit, all 32 members except Spain committed to 5% of GDP, and all now meet the 2% threshold. Secretary General Mark Rutte attributed the target to Trump’s influence combined with Russian pressure following Ukraine. Credit is deserved for demands predecessors soft-pedaled, for a willingness to create discomfort that diplomatic culture usually forbids.
What Trump omitted, and what the room knew: the 5% commitment targets 2035, not immediate implementation. The trajectory is real, but the timeline extends well beyond Trump’s term and depends on sustained political will across thirty-two democracies with competing priorities. The buildup responds to Ukraine as much as American hectoring, complicating simple credit attribution. More consequentially, Trump explicitly questioned whether allies would defend America if attacked: “I know we’d be there for them. I don’t know that they’d be there for us.” This grievance about allied reliability simultaneously communicated American conditionality to partners depending on Article 5 guarantees. Finnish President Stubb’s visible alarm, his immediate effort to seek clarification from Senator Graham, reflected genuine uncertainty about what conditional American commitment means for a country sharing an 830-mile border with Russia. Graham’s dismissive response—that Europeans worry “from the moment they wake up until they go to sleep”—confirmed rather than dispelled concern.
Alliance value depends on credibility, credibility on perceived unconditional commitment. Deterrence rests on adversaries believing attack on one triggers response from all, without calculation, without hesitation, without conditions that might go unmet. Public questioning of allied reliability erodes this foundation even when framed as complaint rather than threat. Trump extracts greater contributions while degrading the asset being leveraged, like a landlord raising rent by suggesting he might not fix the locks. The tenant pays more and sleeps worse, an arrangement that works until the tenant finds another building.
European discussions of French-British nuclear guarantees as alternatives to American protection suggest counterparties already calculating reduced reliability. The ledger shows increased revenue and depreciated principal, a pattern accountants recognize as liquidation rather than growth. The revenue is real. The depreciation is also real. Which number matters more depends on time horizon, and the room contained people whose time horizons extend well beyond the current American administration.
The Territorial Claim
Greenland as the framework’s breaking point
Trump’s Greenland demands consumed substantial time, revealing either supreme confidence in leverage or fundamental misunderstanding of its limits. He first proposed acquiring the territory in 2019, generating bewilderment and firm Danish rejection. The 2026 framing intensified the demand, making explicit the threat structure that previous iterations had only implied. The strategic logic contains genuine validity: Arctic positioning between the United States, Russia, and China matters as ice retreat opens shipping lanes and resource access. American capabilities exceed Danish defense capacity. Monroe Doctrine continuity connects to two centuries of hemispheric exclusion. The argument that Greenland represents “a core national security interest” is not absurd. The method of pursuing it generates costs the logic does not address.
For domestic audiences, Trump invoked patriotic themes. His complaint that America “gave it back” after World War II, his question “how stupid were we,” positioned acquisition as unfinished business rather than imperial overreach. The framing connected to deep patterns viewing the Western Hemisphere as naturally American sphere.
The room heard an ultimatum. “You can say yes and we will be very appreciative, or you can say no and we will remember.” Trump’s repeated insistence that he would not use force, stated three times while cataloging military superiority, created the opposite impression through obsessive denial. New battleships “100 times more powerful” than World War II vessels, weapons rendering Venezuelan defenses inoperable, a $1.5 trillion military budget: reassurance and threat arrived in the same breath.
Russian Foreign Minister Lavrov exploited the demand within hours, drawing Crimea parallels that will outlast the specific controversy. Every Western criticism of Russian territorial aggression now carries a footnote the size of the world’s largest island. The moral vocabulary the West uses to describe international order—sovereignty, territorial integrity, the illegitimacy of coerced border changes—has been compromised by the leader of the Western alliance demanding precisely what the West condemns when Russia does it. The propaganda gift will compound for years, cited whenever Western officials invoke principles that Greenland renders situational. Danish Foreign Minister Rasmussen declared American ownership “a red line,” demonstrating that some counterparties resist regardless of pressure. European defense discussions accelerated as allies calculated what American territorial ambitions implied for their own sovereignty.
The framework that succeeded in pharmaceutical negotiations and tariff disputes shattered against territorial sovereignty. The shards cut in directions Trump did not anticipate and domestic audiences will not see until adversaries have finished exploiting them. Leverage that works through economic pressure assumes counterparties will calculate costs and benefits rationally. Denmark calculated and refused. Russia calculated and weaponized. The hypothesis that American leverage is universal encountered its falsifying instance, visible to everyone in the room and invisible to everyone watching at home.

The Questions He Could Not Script
Where prepared confidence met unrehearsed reality
Prepared remarks permit controlled framing. Questions introduce variables preparation cannot eliminate. Borge Brende’s queries forced Trump to address topics his speech had avoided, and the gap between scripted confidence and responsive qualification revealed the framework’s awareness of its own limits. The theatrical shift from monologue to dialogue changed what the audience could see, and what they saw was a performer encountering material he had not rehearsed.
Brende opened with recession risk. Trump’s response introduced uncertainty absent from his triumph narrative: “Sometimes you get hit unexpectedly and there’s nothing you can do about it.” He invoked the pandemic, recalled polling showing him unbeatable until “the following day, I was told to stay tuned because there’s something really bad happening in China.” The admission that “we need a little luck” contradicts the control narrative where American success flows from American choices and Trump’s dealmaking genius. Luck is what happens to people who cannot control outcomes. Under questioning, Trump admitted membership in that category, a concession no prepared remark had approached.
Debt sustainability produced similar hedging: growth as solution, fraud elimination in Minnesota as expense cutting, no structural reform mentioned. The answer revealed no fiscal strategy beyond the assumption that growth will outpace obligations indefinitely, an assumption requiring sustained favorable conditions Trump had just acknowledged he cannot guarantee. The prepared remarks presented mastery; the Q&A revealed hope dressed as policy.
Ukraine generated the most significant deviation from confidence. The war “was going to be one of my easier ones,” Trump admitted, an expectation unfulfilled despite eight other conflicts he claims settled. “Tremendous hatred” between Zelensky and Putin resists dealmaking logic; Trump described it as “not good for settlements” with the understatement of someone discovering that emotion defeats transaction. “If they don’t get this done, they’re stupid” acknowledges that counterparties may choose courses Trump considers irrational, that his framework assuming rational response to incentives encounters limits when hatred rather than interest drives decisions.
The questions and Trump’s responses merit enumeration:
- Recession Risk: “We need a little luck”
- Debt Burden: Growth and fraud elimination, no structural approach
- China Relations: Personal rapport with Xi, no policy framework articulated
- Greenland Path: Continued assertion, no route to Danish consent identified
- Ukraine Timeline: “Reasonably close,” complicated by “tremendous hatred”
- Gaza Durability: Conditional on Hamas disarmament or being “blown away”
Each answer shares structure: confident framing dissolving into contingency upon examination. Growth depends on luck. Debt reduction depends on growth. China depends on personal relationships. Greenland depends on capitulation. Ukraine depends on hatred yielding to rationality. Gaza depends on Hamas abandoning armed resistance that defines its organizational identity. The accumulation of dependencies suggests fragility the prepared remarks suppressed, a framework resting on foundations its architect cannot secure.
Those who stayed for the full session understood what those who tuned out after the speech did not: the confident framework rests on assumptions its architect knows may not hold. The prepared remarks delivered maximalist claims calibrated for domestic celebration. The Q&A revealed caveats that sophisticated observers require for accurate assessment, the fine print that domestic audiences never read but international audiences cannot afford to ignore.
The Leverage Hypothesis Under Examination
Trump’s address functions as a hypothesis about American power, testable against evidence the room possessed and the television audience did not. The hypothesis holds that leverage deployed across economic, military, and diplomatic domains can extract concessions from allies and adversaries while maintaining the prosperity that makes extraction sustainable. The hypothesis further assumes that leverage is fungible, that success in one domain transfers to others, and that counterparties lack alternatives sufficient to resist. Six domains provided data. The data suggests where the hypothesis holds, where it requires qualification, and where it fails tests the room could grade immediately.
The machinery of reduction works. Unilateral executive action shrinks employment and dismantles regulation without external cooperation. The energy advantage operates from geological foundations, generating leverage transferable to every negotiation. These domains confirm that American action unconstrained by counterparty compliance achieves objectives reliably.
The tariff arithmetic and investment claims occupy intermediate territory. Tariffs alter flows, but effects are complex, adaptation proceeds, and announcement diverges from execution. Leverage works while creating information asymmetries that useful narratives exploit. The hypothesis holds conditionally, dependent on audiences lacking context.
The alliance ledger and territorial claim reveal failure conditions. Extracting contributions while questioning reliability degrades credibility. Demanding sovereignty while adversaries exploit the demand generates responses reducing leverage elsewhere. The hypothesis succeeds until counterparties find alternatives or adversaries convert American coercion into American liability.
The room understood all of this. Sophisticated observers heard a performance designed for less sophisticated consumers, recognized gaps between claim and verification, and adjusted accordingly. Some will accommodate because resistance costs exceed compliance. Some will seek alternatives because unpredictability defeats planning. Some will exploit opportunities American coercion creates for American adversaries. The responses will vary by counterparty, by domain, by calculation of what accommodation costs and what resistance risks. But the recognition was universal: the rules have changed, and the new rules favor those who can see both audiences simultaneously.
What remains uncertain is whether the hypothesis will be tested to destruction or constraints will emerge before catastrophic failure clarifies them. Trump’s admissions that luck matters, that shocks arrive without warning, that counterparties sometimes choose what he considers stupidity, suggest awareness of boundaries. Whether awareness translates to restraint at boundaries remains the question Davos attendees must incorporate into positioning, hedging, and quiet repositioning against American volatility.
The information asymmetry will not persist indefinitely. Domestic audiences eventually learn what international observers knew immediately, what the room understood while the television audience received only the performance. The question is whether learning arrives through gradual adjustment or sudden correction, through managed repricing or disorderly discovery.
The room’s silence during the speech was not deference. It was calculation.