The Predicament of Modern Gambling
As the centennial of the 1929 Crash approaches, and of the Great Depression that followed, the mix of cultural memory and present circumstances creates a volatile cocktail. The collapse—shuttered brokerages, evaporated fortunes, bread lines—burned itself into the collective imagination, and made speculation synonymous with danger. In the decades since, gambling in almost any form has carried a stigma. Until recently, casinos were confined to distant jurisdictions, lotteries were state-controlled, and market speculation was framed as sober only when disciplined by institutional oversight.
A hundred years later, the cultural position of gambling is inverted. The same behaviors once treated as reckless now exist in the background of ordinary life. Online platforms allow anyone to trade news the way others read it, to bet on games as casually as they watch them, to stake positions in prediction markets the way others doom-scroll social media. The interface is seamless, the increments small, the access continuous. What once required a broker, a bookmaker, or a casino floor now unfolds on phones and laptops beside banking apps and email.
This normalization did not arrive all at once. It followed a long corridor of incremental permissions. State lotteries framed wagering as civic contribution. Casino expansion was sold as economic development. Fantasy sports blurred into sports betting, while commission-free trading apps rebranded speculation as participation. Step by step, the distance between entertainment and risk narrowed until it disappeared. Gambling ceased to appear transgressive. It became just another way of engaging with information, sports, and markets.
The predicament lies in this banality.
Risk is no longer recognized as extraordinary. A bet on the weekend game feels like fandom. A trade timed to a headline feels like staying informed. A position in a prediction market feels like civic engagement, no stranger than scrolling the feed. Yet beneath this ordinariness, the same vulnerabilities that shattered 1929 remain. Mispriced confidence, ritualized control, and emotional displacement are not erased by new technology; they are amplified by it. The volatility that once flashed on ticker tape now streams through notifications, demanding constant attention and inviting constant action.
The contrast with the Depression era could not be sharper. Then, the public recoiled from gambling, treating it as a force to be contained. Today, the same impulse is woven into everyday routine, its risks masked by design. The consequence is not only personal harm—financial ruin, relational collapse, psychological strain—but systemic fragility. The century-old lesson is that speculative fever never stays private. When risk is misread at scale, contagion spreads. Then it toppled banks. Today it travels through platforms, multiplied by networks and accelerated by design.
As this anniversary approaches, the challenge is not to abolish gambling but to understand it properly. It is not merely entertainment, nor simply pathology. It is a structural engagement with volatility, one that demands frameworks capable of mapping failure before collapse occurs. Existing clinical systems are not built for this. They frame gambling as addiction, as impulse disorder, or as a subset of substance-use pathology. Such framings miss the architecture of control and collapse that defines modern gambling’s grip.
Meanwhile, the DSM-6 is expected to reposition gambling disorder away from the margins of addiction and toward the center of structural risk mispricing. Furthermore, male suicidality and complex trauma will likely be reframed as distinct architectures rather than secondary symptoms. My proposal anticipates the shift. It treats gambling not as chemical compulsion but as cognitive misalignment, not as weakness but as structural distortion. It is expressly designed for pre-compliance with the coming standard. The task is to build a treatment protocol that does not merely suppress behavior but restores competence inside volatility.
The threat of an even Greater Depression is very realistic as I write this. With luck, a century after the Crash, the same mistakes may not be redistributed under new names. As desperation rises, the temptation to mismanage risk will only grow.
Diagnostic Arc
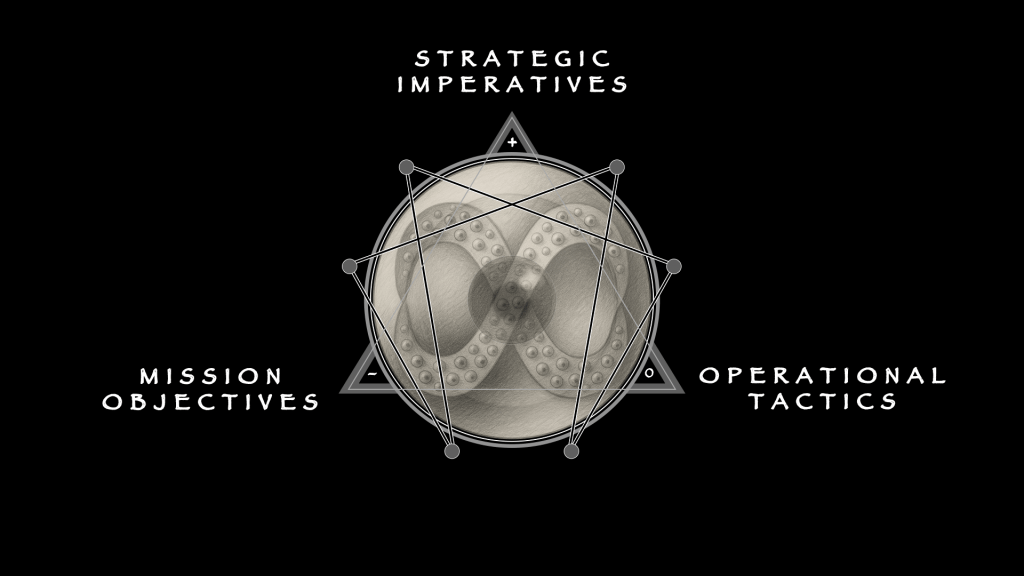
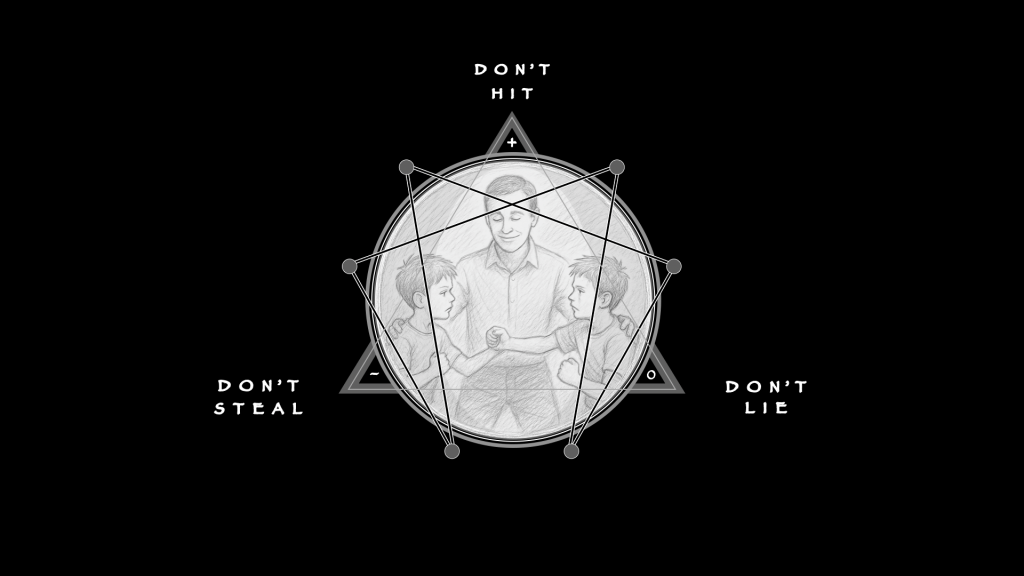
Diagnosis begins with structure, not with story. Gambling does not announce itself as pathology; it embeds into routine. A wager accompanies the game, a trade rides the headline, a prediction market scrolls like any other feed. What distinguishes ordinary engagement from collapse is not the presence of risk but the distortion of process. The Enneagram provides the geometry to see this. Each point describes a lawful function, a way the system is meant to handle pressure. Each can also be tracked for how it bends under strain, producing failure patterns that repeat with unsettling precision.
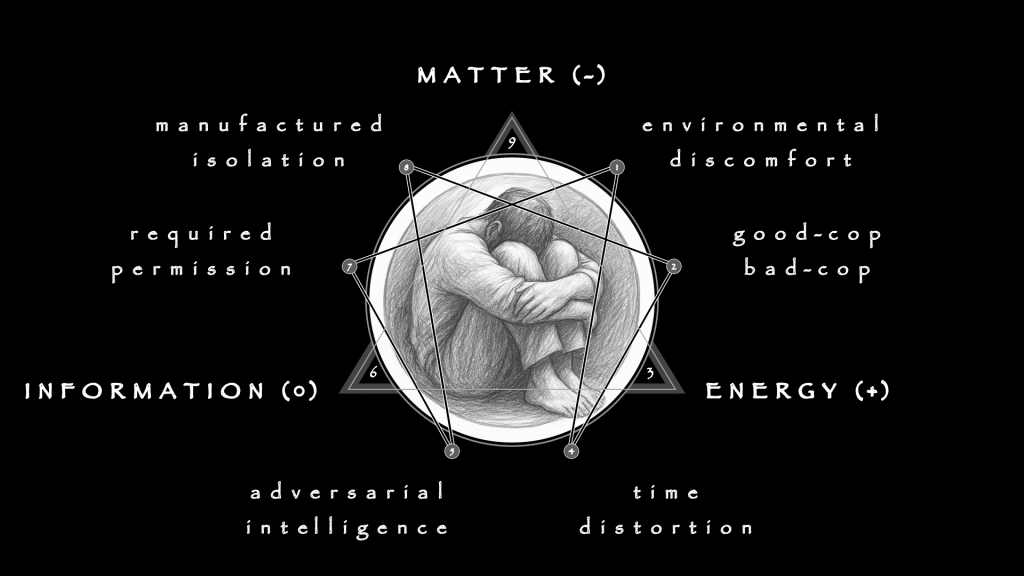
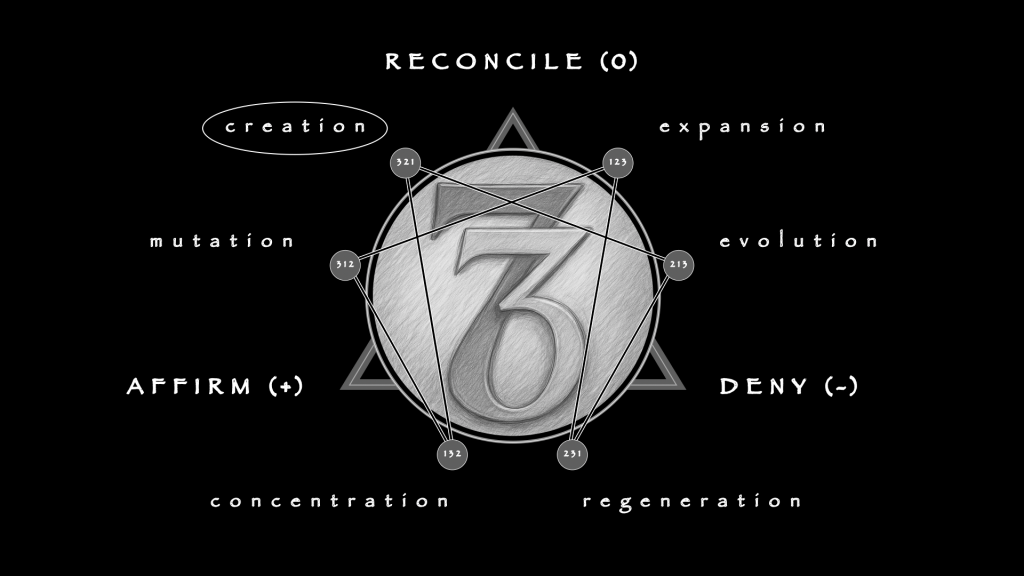
Gambling dresses itself as risk and reward, but diagnosis strips away the glitz. Diagnostics, however, must affirm (+) risk in its totality so that volatility can be mitigated early. Its task is containment, or the 132 triad of Concentration. Among professionals (the target role model), management outranks risk: without it, there is only play, not discipline. Once gambling becomes a disorder, management must be re-installed before it can be re-learned.
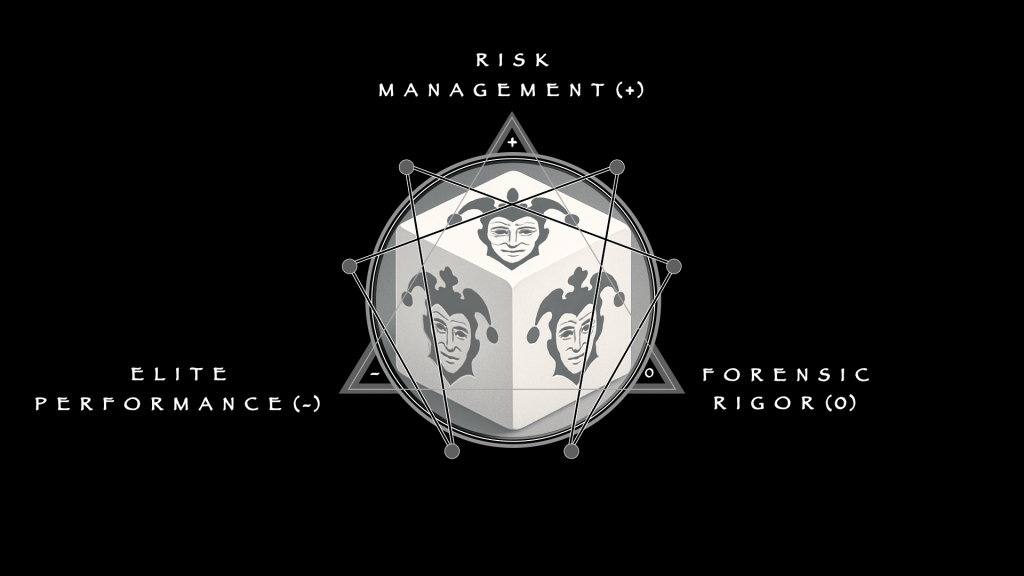
Containment, however, cannot live in private thought, but requires the clinic as the medium. Ad hoc methods deserve suspicion, for their successes are not as reproducible as their failures. In a proper medium, impressions are reconciled (0) as record. Behaviors become notes, patterns become criteria, and judgments become findings that can travel between practitioners. Forensic rigor is not an accessory but the atmosphere of diagnosis. It allows management to be shared, transferred, and held accountable.
Only then does performance as denial (-) appear. The clinician denies distraction: resists being pulled back into stories of wins and losses, resists being swayed by affect or institutional noise. Elite performance in this sense is bounded; it has no sovereignty of its own. It is merely an effect of rigor, a refusal to let volatility govern once concentration has been achieved. Diagnosis is not theater. It is management affirmed, rigor reconciled, and denial held as impulse control.
Diagnosis reveals Six Distortions.
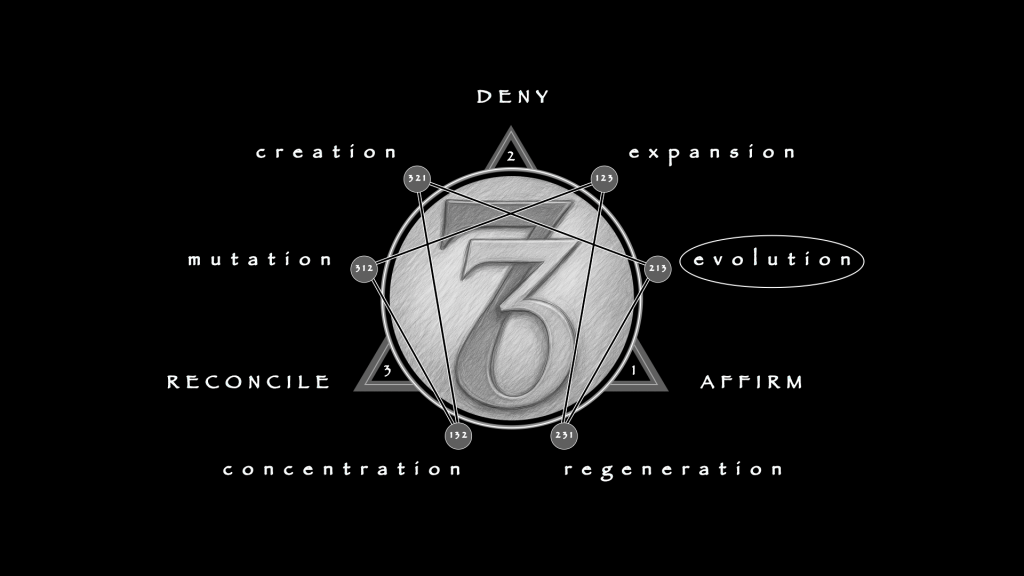
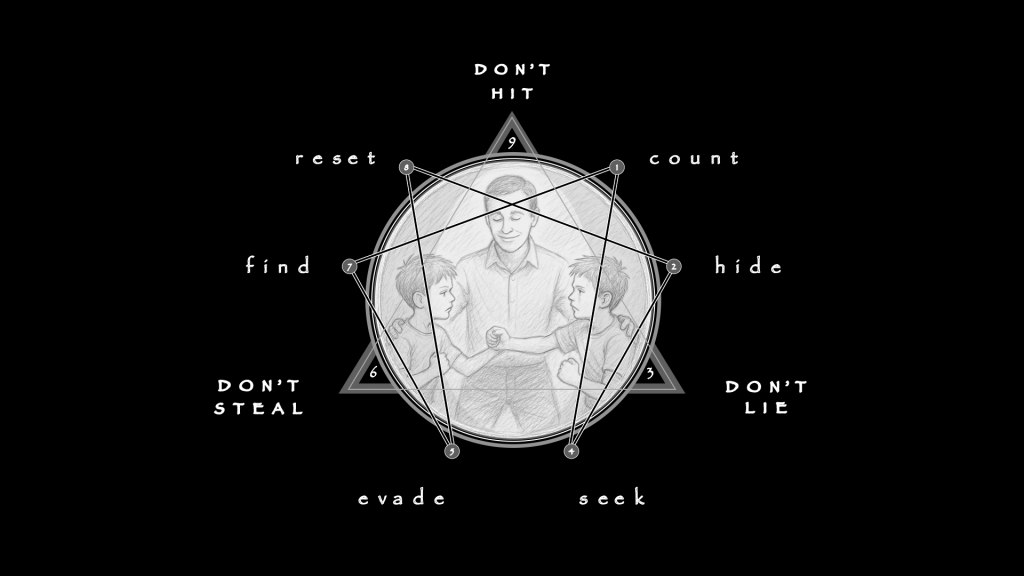
They are not symptoms but structures—predictable collapses of logic where the perception of edge falters. Each describes a lawful process, including how it fails when volatility is misread. Taken together, they comprise a diagnostic cycle: Expansion shrinks into Overreach, Evolution ossifies into Ritual, Regeneration disguises itself as Impulse, Concentration disperses into Theater, Mutation collapses into Mood Regulation, and Creation abdicates into Dependency. The map does not judge; it clarifies. It shows how ordinary risk-taking, left unchecked, folds into compulsion.
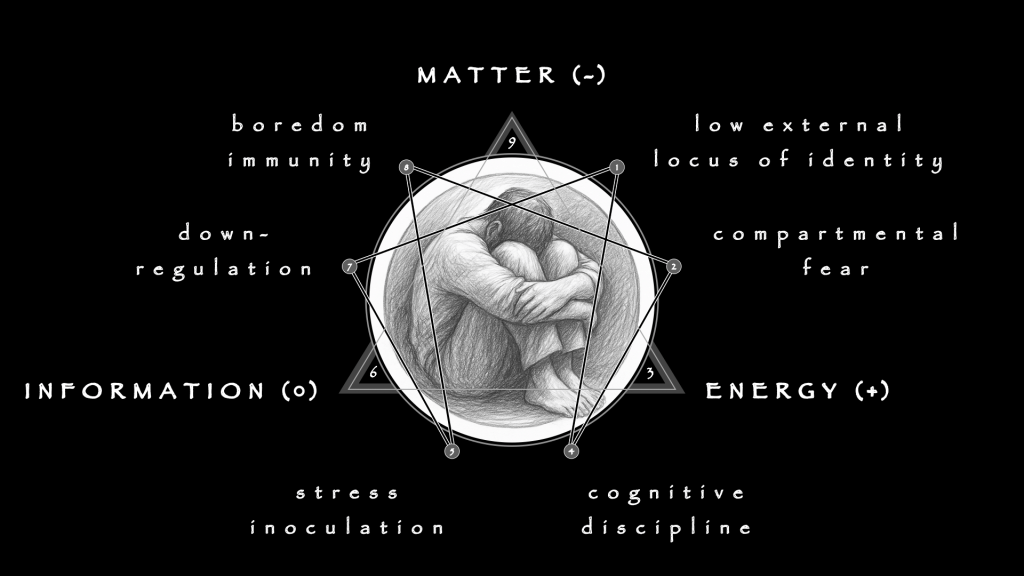
The 1st Distortion results from primal Expansion, any system’s outward push into new ground. In gambling, this urge aims to probe a field, to test possibility, stretching outward not to dominate but to discover. Properly expressed, it is experimental: small positions across diverse opportunities, exploratory wagers to sample conditions, tentative exposures to feel how volatility responds. Expansion allows learning before commitment, establishing a buffer where missteps remain survivable. In healthy form, it cultivates curiosity, building capacity to see patterns without believing oneself their master.
Distorted, it collapses into Strategic Overreach. Instead of probing, the actor mistakes elaboration for control. Models pile on models, indicators crowd the screen, research multiplies until it becomes its own justification. A trader spends dawn hours annotating news, convinced that more inputs guarantee mastery. A sports bettor builds elaborate spreadsheets to prove the bookmaker wrong. Each small win is claimed as confirmation; each loss is rewritten as error in execution rather than evidence of volatility. Expansion, meant to widen horizons, contracts into a self-reinforcing cage. What began as curiosity ossifies into conviction, until collapse is the only teacher left.
The 2nd Distortion results from primal Evolution, which thrives thrives on feedback. It shifts when conditions change, discards what no longer works, adapts strategies to fit the environment. In its healthy form, the urge treats volatility as feedback. A bettor adjusts to new line movements rather than stubbornly clinging to old numbers. A trader reduces exposure when cycles shift, reallocating capital where signals are stronger. Evolution honors flux by moving with it, transforming unpredictability into intelligence. It sustains resilience by treating change as signal, not threat.
Under strain, Evolution leans into Ritualized Control. Adaptation gives way to choreography. The actor builds routines—always entering a position at the same time, always clicking the same sequence, always opening the same tabs in order. These small ceremonies simulate safety but erase flexibility. A gambler insists on sitting at the same slot, tapping the buttons in his lucky rhythm. A bettor refuses to alter his staking plan, believing ritual protects him. What should be adjustment becomes repetition. Evolution freezes into defense, substituting sameness for stability. The result is brittle security: comforting until it fails, devastating when it does.
The 3rd Distortion may be seen as Regeneration disabled, the ability to metabolize setback into renewal. Loss or failure must not be hidden, but absorbed and redirected. In healthy form, it looks like a trader reducing size after a drawdown to rebuild confidence, or a bettor reviewing losses to refine his model. Regeneration accepts that constraint is part of the cycle. It transforms depletion into discipline, shaping a setback into fuel for future engagement. This is the art of turning adversity into resilience, of making each failure a hinge for recalibration.
Bent back on itself, Regeneration becomes Justified Impulse. Instead of metabolism, the actor settles for narrative. Another wager is excused as harmless: “It’s just for fun.” A streak of trades is reframed as deserved: “I’ve earned this risk.” Rationalization replaces reflection. Small impulses multiply because each is shielded by story. Larger exposures are reframed as temporary indulgences. A student clicks through another spin, whispering that it doesn’t matter; a bettor justifies doubling down as fair payback. Regeneration disappears beneath the cover of permission. The lawful cycle of recovery collapses into ongoing excuses that keep pace with the losses, but never correct them.
The 4th Distortion arises from Concentration, that would otherwise channel attention into precision. The adaptive version sharpens focus, narrowing scope to refine accuracy. In markets, it means honing in on a few instruments and mastering their rhythms. In betting, it means calculating probabilities carefully, limiting wagers to situations with clear edge. Concentration tempers volatility by condensing it into clarity. Properly expressed, it disciplines energy, directing risk into clean lines of action where outcomes can be measured against standards.
The maladaptive version disperses Concentration into Status-Driven Risk. Focus shifts from precision to performance. The wager becomes a symbol of identity, not an exercise in probability. Escalation is pursued not for return but for recognition. The bettor posts his slips for admiration; the trader boasts of his positions on forums; the prediction market player declares foresight to peers. A young man raises his stakes not because the model demands it but because the crowd is watching. Each risk becomes theater, each loss reframed as proof of boldness. Concentration, meant to compress into clarity, balloons outward into spectacle. Risk becomes self-expression rather than measured action, until identity is staked as heavily as capital.
The 5th Distortion results from the lawful inevitability of Mutation which, to a gambler, means the art of transforming raw hazard into a desired outcome. Surprise is not resisted but dramatically converted, for better or for worse. In healthy form, it means revising systems after shocks, integrating volatility as new information. A trader treats a market swing as a chance to refine, not retreat. A bettor sees an unexpected outcome as data for recalibration. Mutation bends randomness into resilience, building strength from the unexpected.
Distorted, the process devolves into Affective Displacement. Here risk is consumed as mood regulation rather than adaptive response. The wager functions like a pill: to numb boredom, to chase excitement, to steady anxiety. Volatility ceases to be signal; it becomes self-medication. A worker checks odds compulsively on his break, not for strategy but for calm. A student spins a wheel late at night, not to win but to escape. Mutation, meant to metabolize disruption, narrows to manipulation of state. The lawful transformation of systems is abandoned for the temporary modulation of feeling. The risk is no longer engaged—it is ingested.
Finally, The 6th Distortion may be understood as the urge, premature, or misapplied, of Creation itself, the constructive climax that closes one cycle and enables another. In practice, it means building durable systems: risk logs, disciplined staking plans, portfolio rules, proven strategies that survive individual variance. Properly expressed, Creation takes the lessons of volatility and crystallizes them into frameworks that hold over time. It generates stability by turning experience into structure.
Creation’s opposite, which leads to ruin, is not destruction, but Surrogate Mastery. Instead of generating structure, the actor outsources it. Algorithms, bots, tip sheets, or influencer signals become the substitute for discipline. Agency is handed off to apparatus, and identity fuses with tools. A bettor follows a subscription feed blindly, convinced the system will protect him. A trader relies on automation he cannot override. For as long as the surrogate holds, mastery feels intact. But when the tool fails, collapse is immediate, because responsibility has already been abdicated. Creation, meant to be generative, becomes dependency disguised as sophistication.

Together these Six Distortions comprise my Failed Edge Diagnostic model. The version presented here is abbreviated. Each is not a symptom but a structure: lawful process bent into predictable failure. The extended version includes a detailed section devoted on risk profiles that is neither a typology nor necessary to elaborate here. What makes the proposed method useful is not moral judgment but its predictive clarity, indicating in universal terms where and how edge will fail.
This clarity also explains why conventional treatments falter. They address surface behavior, not the underlying process. They treat compulsion as addiction, not as structural mispricing of self-belief. The DSM-6 will likely attempt to codify this shift, reframing gambling disorder as a collapse of risk logic rather than a byproduct of chemical compulsion. The diagnostic arc presented here is already aligned with that horizon. It shows how lawful functions bend into failure, and in doing so, it prepares the ground for treatment arcs that do not merely suppress risk but restore competence inside it.
Treatment Arc
A series of Treatment Phases is offered here in the spirit of proposal, not as a finished clinical manual. Its boundaries are theoretical, its methods sketched rather than field-tested. This distinction is crucial. To claim otherwise would collapse the difference between a working hypothesis and an operational program. The lawful scaffold presented here maps perfectly onto the Enneagram precisely to address a predictable structural weakness of other models.
Treatment itself is 231, Regeneration. Collapse is brought into the room as loss. First it is denied (–): illusions cut away, compulsions interrupted. Then it is reconciled (0): what remains is faced without disguise, integrated into a frame that can hold. Only then can it be affirmed (+): a new structure, provisional at first, strong enough to invite re-entry into risk. That is the arc—loss metabolized into capacity. Expansion (123) could only multiply options; Concentration (132) could only narrow them. Treatment requires dismantling and rebuilding in a single process, and only the 231 triad carries that lawfully.
Current clinical practice around gambling disorder is dominated by frameworks inherited from addiction medicine. Abstinence is often framed as the objective, with treatment borrowed from models first designed for substance use. Cognitive-behavioral approaches attempt to identify distortions and substitute rational thoughts. Twelve-step programs emphasize surrender and community reinforcement. These have value, but they were not built to handle compulsions that are architectural rather than chemical. Gambling collapses not because dopamine overwhelms willpower, but because the subject misplaces control—confusing ritual for causality, fluency for edge, volatility for stability. Existing systems can interrupt behavior, but they rarely correct the mispricing of risk logic itself.

The approach outlined here is therefore radical. It does not treat gambling as a moral weakness, nor as a purely neurochemical malfunction. It treats it as a metacognitive failure in how edge is perceived and agency is maintained under volatility. The aim is not abstinence but competence—the ability to operate inside risk without collapse. Where current systems aim to reduce exposure, this arc teaches how to hold velocity inside volatility. Where others prescribe restraint, this one prescribes structure. It proposes a firewall between language and loop, a phased discipline that begins with NLP as scalpel and pivots to the OODA Loop as suture. Such a model will not be easy to implement. It demands rigor from both clinician and patient. But if successful, it restores risk as a usable force rather than a destructive compulsion.
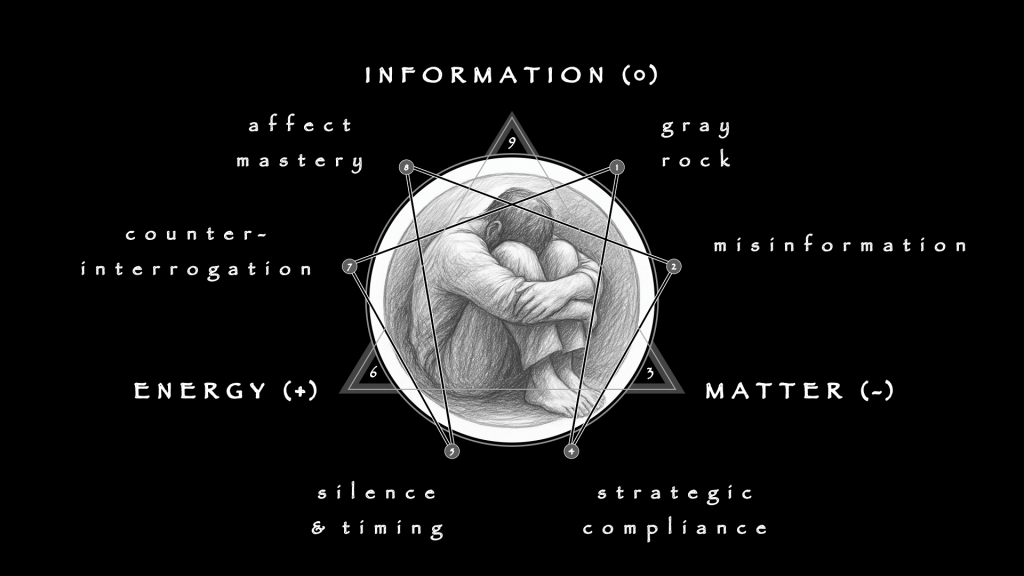
In the 1st Phase, work begins with Extraction from Volatility. The immediate task is containment. Volatility here means not just market swings or betting slips but the informational overload of screens, cues, and rituals. These streams flood the nervous system, making judgment impossible. Extraction creates friction where the environment has been frictionless. Limits on access, disruption of cues, and enforced pauses interrupt recursive loops. This does not announce retreat but tactical preservation. The patient must feel something is being protected, not stripped away. Physiology leads cognition: stabilizing sleep, reducing stimulus, grounding routines. Language is used only to puncture urgency when it surfaces, never to soothe or rationalize. The scalpel cuts quickly and is withdrawn. The priority is to halt momentum, not to explain it.
The 2nd Phase entails Ritual Disarmament. Compulsions are rarely chaotic; they are structured by routine. Which tab opens first, which sequence of actions is followed, which small gestures precede the wager—these are not casual but ceremonial. They simulate safety. Disarmament proceeds not by ridicule or confrontation but by substitution. Patterns are inverted, sequences altered, gestures replaced. The hand must move differently; the rhythm must break. Safety dissolves when sameness no longer guarantees comfort. The actor learns discomfort deliberately, practicing control without ritual anchors. The work here is practical: disrupting choreography until the false shield of ritual is exposed as empty.
The 3rd Phase turns inward via Somatic Reset and Reframing. The body must learn neutrality. Breathwork, contrast exposure, and boredom drills teach the nervous system to settle without external stimulus. The ability to downshift becomes the baseline skill. Only against this calm backdrop can cognitive reframing occur. Distorted beliefs lose their hold when tested against physiological stability. What felt urgent in stimulation is revealed as hollow in stillness. This is also the firewall moment. Once neutrality is installed, language must end. The clinician seals the boundary with a ritual phrase: “Language is logbook. The loop is the tool.” From here on, NLP is banned. Reframes, metaphors, and verbal smoothing are corrosive. The scalpel is retired. OODA becomes the suture.
By the 4th Phase, treatment must shift outward into Frictional Reintegration. The system is now exposed to controlled doses of volatility. Simulated bets, practice trades, decision drills under mild pressure—each is designed not to eliminate risk but to test whether the loop holds under load. The outcome is secondary; coherence is primary. Can the subject Observe, Orient, Decide, and Act without escalation? Can drift be noticed mid-loop, and corrected in real time? Volatility here is a training partner. It stresses the system just enough to reveal whether discipline holds. Reintegration is not abstinence but rehearsal. The actor learns to pace risk rather than to avoid it.
The 5th Phase, penultimate in the series, advances to Modular Risk Reintroduction. Exposure now moves into real-world contexts—actual trades, real wagers, market positions—but contained within strict modules. Each module has boundaries: a set number of actions, a capped stake, a defined window of time. The patient learns that risk can be engaged without becoming totalizing. Each module ends by design, not by compulsion. The OODA Loop runs without supervision, triggered by the actor himself. Drift is logged, not disguised. The act of disengagement becomes as important as the act of entry. Competence here is measured not by winnings or outcomes but by the ability to return to baseline at the close of each module.
The arc culminates in the 6th Phase, Structural Autonomy. To exit this stage, the patient must be capable of running decision cycles under live pressure without external scaffolding. External architecture is built not as a crutch but as a buffer: dashboards, accountability systems, tempo flags, reflective practices. These hold the frame when intuition falters. The subject also learns to run loops backward in post-mortem: Where did observation break down? Which orientation failed? Was the decision lagged or rushed? Did action leap ahead of awareness? These reflections compress experience into structure, preventing drift from compounding. Autonomy here does not mean absolute control—control is always temporary. It means sovereignty: the capacity to act under risk without collapse, to recognize drift without denial, and to restore balance without rescue.
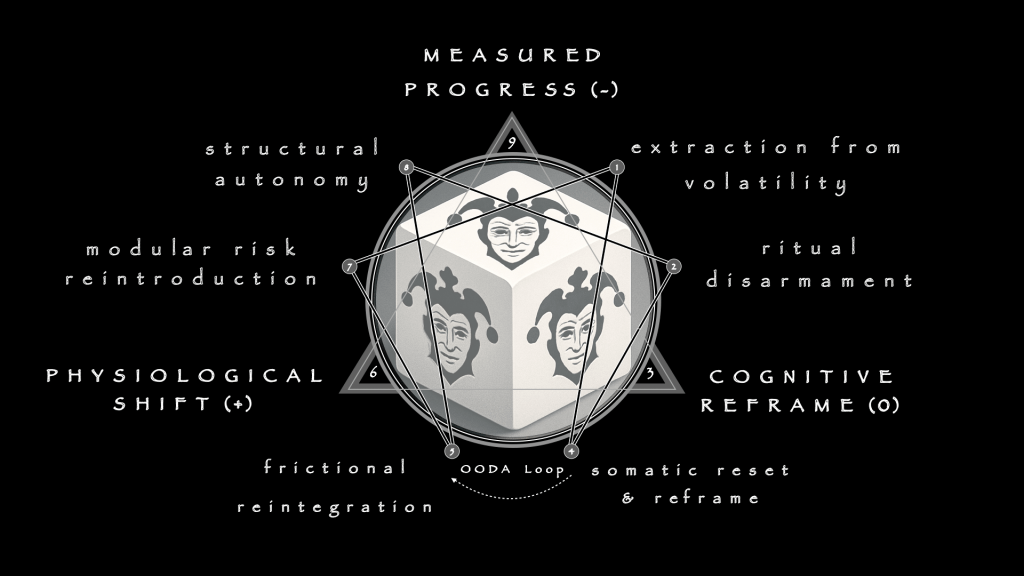
These Six Treatment Phases form a counter-arc to the Diagnostic cycle. Extraction, Disarmament, Reset, Reintegration, Reintroduction, Autonomy—together they offer a path from collapse to competence. This proposal does not claim final authority. It sketches what repair might look like if the Enneagram’s geometry is applied not to personality but to risk logic itself. It is radical, but the need is clear. Where existing systems seek abstinence, this one seeks readiness. Where others emphasize compliance, this one emphasizes sovereignty. The measure of success is not the absence of risk but the presence of discipline that holds inside it.
The Broader Corpus
The Failed Edge Diagnostic Model is not a departure from my prior work but its continuation. Each of the Distortions mapped here belongs to the same operational geometry that has anchors the rest of my work. The Law of Three and the Law of Seven still govern. Only the arena is novel: risk engaged as gambling, trading, and prediction markets. The material may shift, but the geometry does not.
The bifurcated design—diagnostics precise, treatment provisional—aims to preserve fidelity to the method. Diagnostics can be mapped with rigor because failure repeats. Treatment remains scaffolding because re-entry requires stress-testing. That asymmetry is not a flaw but a feature. It mirrors the geometry itself: clarity first, experiment after. To mistake one for the other would collapse the firewall that protects the work from wishful thinking.
Generously speaking, the institutional horizon confirms my orientation.
The DSM-6 will, with the best of intentions, attempt to recast gambling disorder, male suicidality, and complex trauma as structural expressions rather than symptomatic debris. Where clinics have spoken of addiction or impulse, they will soon speak of architecture. In that sense, my contribution to the arena, this Failed Edge model of diagnosis and treatment is beyond pre-compliant. Not only does it refuse to wait for categories to change,, and not only does it demonstrate the logic that those categories will eventually adopt, it also has no known peer.